We've tried every Samsung phone, and these are the best picks for you in 2025
The best Samsung phones in 2025 focus on the company's strengths, like long software support promises, great features, and top-notch hardware quality.

At a glance
1. Best overall
2. Best flagship
3. Best foldable
4. Best premium foldable
5. Best mid-range Galaxy
6. Best budget Galaxy
How to choose
Android Central has been around longer than Samsung's Galaxy series of smartphones, and we have tried every single model since their release. We know how to tell which ones are great and worth your money, and we've put them all through their paces, from the Samsung Galaxy S25 series to the Galaxy Z Fold 7.
Looking for a great place to start when choosing from the best Samsung phones? The most up-to-date features and powerful software, along with the sleekest hardware, comes with the Galaxy S25 Ultra. The Galaxy S25 Edge is a slimmer, lighter, and cheaper option that's still premium. We can't count out the classic Galaxy S25 and Galaxy S25 Plus, either.
There are also the Flip and Fold lines, which offer a unique design proposition with handy inner and outer screens. On the way is the Galaxy Z TriFold, which offers a 10-inch display for those who are willing to fork over the dough for a futuristic-looking phone. Conversely, Samsung its A series devices to serve as a wonderful entry point into the Galaxy world without breaking the bank.
Between the reliable Galaxy S series, folding Galaxy Z series, and budget Galaxy A series, there's sure to be something for everyone here. Let's break down all our picks for the best Samsung phones below.
At a glance

Best overall
Samsung's latest Galaxy S25 Ultra includes a blazing-fast Snapdragon 8 Elite for Galaxy processor, which enables brand-new Galaxy AI features. It has a bigger 6.9-inch display and retains S Pen support. Samsung rounded off the corners to make it more palm-friendly, ensuring that this big, beautiful phone is comfortable to hold in your hands.

Best flagship
The Samsung Galaxy S25 might look the same as the Galaxy S24, but there are some neat changes under-the-hood. It starts with the Snapdragon 8 Elite for Galaxy processor and 12GB of memory, which combine to enable flashy Galaxy AI features. Samsung's base-model flagship is thinner, lighter, and more compact than ever before.

Best foldable
The larger, edge-to-edge cover screen and wider main screen on the Galaxy Z Flip 7 might be enough to make this the perfect foldable for everyone. It's more durable than ever, with an IP48 certification and a new hinge design.

Best premium foldable
The Samsung Galaxy Z Fold 7 features a redesigned chassis that's thinner and lighter than ever before, all while adding crucial processor and camera upgrades. With a wider cover screen, the foldable is now just as versatile opened or closed.

Best mid-range Galaxy
Mid-range refers more to the price here than the phone itself because the A56 gives you a great camera, outstanding battery life, water and dust proofing, and expandable storage in a phone that costs well under $500. It's quite the bargain!

Best budget Galaxy
Whether you want something cheap for the jobsite or just don't need a ton of performance out of your phone, the Galaxy A16 5G is a strong budget pick with a nice screen, decent main camera, and even 5G support.
Best overall

Specifications
Reasons to buy
Reasons to avoid
If only the latest and greatest will do, the Samsung Galaxy S25 Ultra is the phone for you. It houses the most powerful processor Samsung has ever put in a phone — that's the Qualcomm Snapdragon 8 Elite for Galaxy processor — which even puts Apple's latest processors to shame. It's based on Qualcomm's laptop chips and enables new Galaxy AI features. It's also future-proofed and will help Samsung deliver new AI features in the years to come with its seven-year OS upgrade guarantee.
If that wasn't enough to sway you, the Galaxy S25 Ultra has a bigger 6.9-inch display with the same great tech as last year's model. It's a 120Hz, variable refresh rate panel with QHD+ resolution and inbuilt S Pen support. There's also a new, 50MP ultrawide camera for your photography needs. Plus, the new rounded corners ensure that your palms won't get uncomfortably poked while holding this big, beautiful phone.
Of course, the Galaxy S25 Ultra is a massive phone with a price tag just as big, so read on if you're looking for something different.
Best flagship

Specifications
Reasons to buy
Reasons to avoid
Some people want all the bells and whistles, but a lot of people just want a phone that works great and will last a long time without slowing down. That's where the Samsung Galaxy S25 comes in. I recommend it as the more sensible option for people who want a great flagship phone that's both smaller and cheaper than the Ultra variant.
Despite that, the Galaxy S25 shares many of the things that make the Galaxy S25 Ultra great. That includes the Qualcomm Snapdragon 8 Elite for Galaxy chipset, new Galaxy AI tools, and a seven-year OS upgrade guarantee. You get all this for the same starting price as the Galaxy S24, too.
The Galaxy S25 is equipped with the same 6.2-inch AMOLED display as the Galaxy S24, with a 120Hz variable refresh rate. That isn't a bad thing, because the Galaxy S25 is smaller, thinner, and lighter. It's one of the best compact flagships on the market, if not the best.
Best foldable

Specifications
Reasons to buy
Reasons to avoid
While we're typically more inclined to recommend a Motorola Razr as the best flip phone, the Samsung Galaxy Z Flip 7 takes major steps forward. Samsung's flip phone now features an edge-to-edge cover screen measuring 4.1 inches, and that's actually bigger than Motorola's Razr Ultra 2025. The main display is wider too, making it feel like a Galaxy S25 Plus on the inside. Plus, the new Exynos 2500 chipset is just as good at crushing AI tasks and gaming performance as the competition.
Software has always been a reason to pick a Galaxy Z Flip model over something from Motorola, and it's even better this year. Samsung launched the Galaxy Z Flip 7 with One UI 8, based on Android 16. It became the first Galaxy phone to run One UI 8, alongside the Galaxy Z Fold 7, putting the Galaxy Z Flip 7 ahead of the curve. From there, you'll get seven years of full Android OS upgrades and security updates. That's more than double the amount you'd get with a Razr.
Like its predecessors, the Galaxy Z Flip 7 is water-resistant and is built to withstand the rigors of everyday life, but that also includes protection against larger solid particles. While it's not quite the dust protection we've been asking for, the IP48 rating for the Flip 7 is solid, and Samsung's hinge design and stability are best-in-class.
The list of improvements also includes the Now Bar, Now Brief, and Gemini Live accessible from the cover screen, plus a snappier 120Hz refresh rate. You also get a slimmer and lighter design compared to prior Samsung foldables, making the Galaxy Z Flip 7 easier to stow in a pocket or bag. It's the best Samsung flip phone ever, and it's sure to captivate longtime foldable users and newcomers to the form factor.
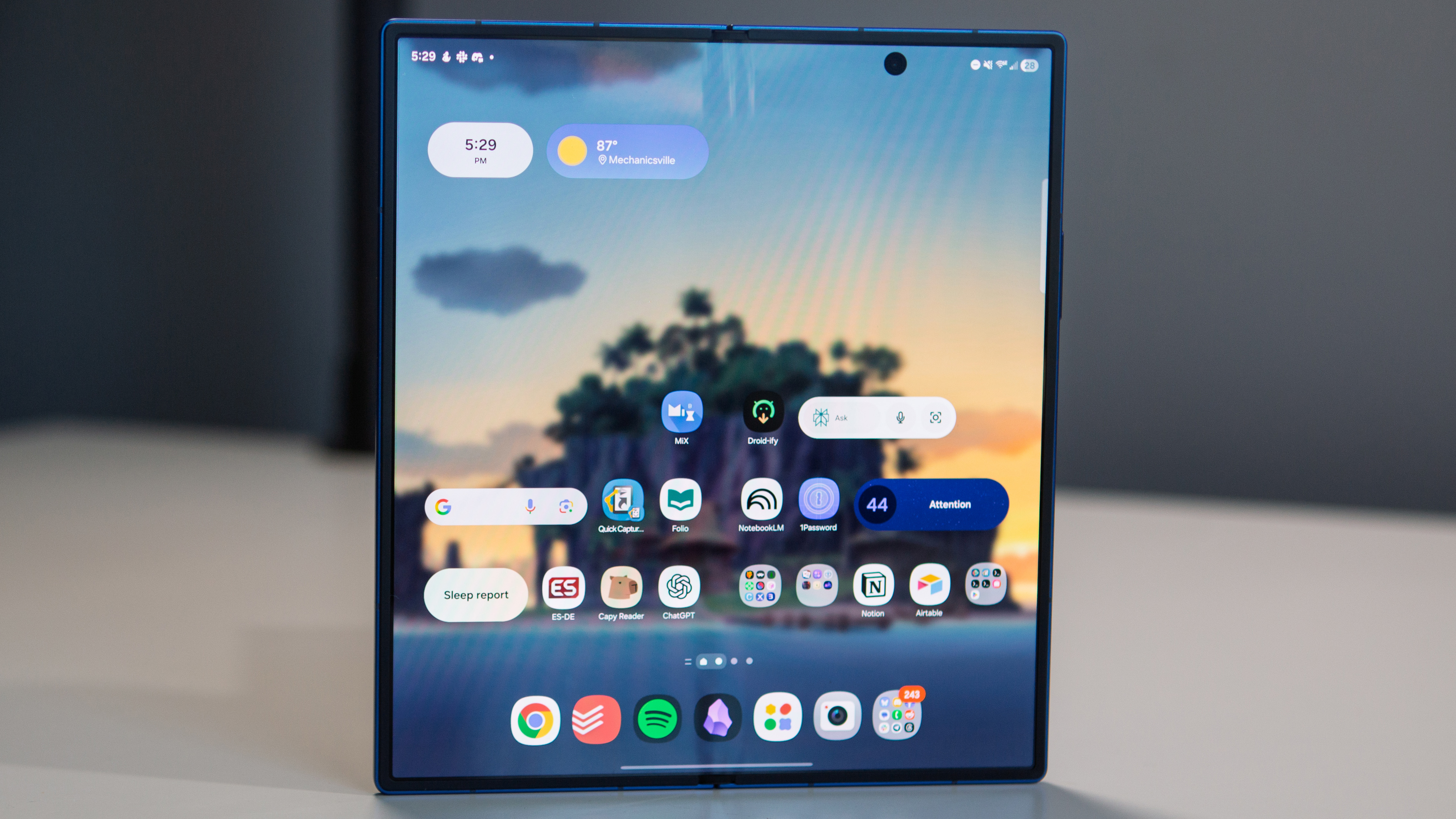
Best premium foldable
Specifications
Reasons to buy
Reasons to avoid
The Samsung Galaxy Z Fold 7 is an impressive overhaul that builds on the success of the Galaxy Z Fold 6 Special Edition, released only in China and Korea. Now, the slim and lightweight chassis that model introduced is coming to everyone on the Galaxy Z Fold 7. At only 215 grams, it's actually lighter than the heavyweight Samsung Galaxy S25 Ultra. It's not even that much thicker, measuring 8.9mm when closed.
As such, the Galaxy Z Fold 7 is a big foldable you can finally use like a normal smartphone. The cover display is even wider this year, making the outer screen easier to type on and use for quick tasks. The inside is a stunning 8-inch AMOLED panel with a crease that's harder to see than ever before. We lost S Pen support for the sake of thickness, but I think it was worth it.
While the battery size is the same as the Z Fold 6, the battery life is still pretty good. Power users who utilize the main screen all the time might need to recharge to get through a full day, but battery life is still solid for moderate users. There's now a new Qualcomm Snapdragon 8 Elite for Galaxy chip that brings impressive performance to Samsung's best foldable.
We wish Samsung would have improved the charging speeds, though, as it's still stuck at 25W while competitors like the OnePlus Open charge three times faster. There's also no magnets for Qi2 support, which is a bummer as the Google Pixel 10 Pro Fold is launching soon with that feature.
Paired with a new 200MP main camera sensor, the Galaxy Z Fold 7 is Samsung's most complete foldable ever. It should last for years to come with IP48 certification for durability and seven years of Android OS upgrades.
Best mid-range Galaxy

5. Samsung Galaxy A56
Our expert review:
Specifications
Reasons to buy
Reasons to avoid
Like the Galaxy A55 before it, the Samsung Galaxy A56 continues the legacy of the top-tier A-series mid-range smartphones, bringing you great cameras, outstanding battery life, and expandable storage in a phone that costs under $500. If you already own a Galaxy A55 though, you might want to skip this as it doesn't really offer any meaningful upgrades.
The 2025 refresh brings with it a few minor upgrades for roughly the same cost. For starters, it now gets Gorilla Glass Victus Plus for the front and back panels, while most other phones at this price range get 2013's Gorilla Glass 3 or something equally old. The next change is the SoC, which is now an Exynos 1580 chip built on the 4nm process.
The display on the Galaxy A56 is larger at 6.7 inches, including a peak brightness level bump. The rest of the specs and features are more or less the same as before. There's a 50MP main camera, an IP67 rating for dust and water-proofing, and the phone comes with Android 15. Samsung is promising seven years of updates for the A56, which is very good for a sub-$500 smartphone.
Best budget Galaxy

Specifications
Reasons to buy
Reasons to avoid
The Galaxy A16 5G isn't Samsung's cheapest Galaxy phone, but it isn't far off. Even so, it gets better update support than some flagships with Android 14 out of the box and six years of software updates promised. It has a 6.7-inch AMOLED display with a 90Hz refresh which looks nice, and Samsung has switched from the Mediatek Dimensity 6100+ chipset to an Exynos 1330 chip which should be more potent.
The camera system is decent for this level of phone with the ability to snap some solid pictures in good lighting thanks to the 50MP main sensor. You can take photos all day with the large 5000mAh battery, and storage can be expanded with a microSD card. Samsung ditched the 3.5mm jack this time around, which is a huge shame, but at least there are some dirt-cheap (and really good) wireless earbuds available these days.
This phone supports 5G and if you get the version made for the U.S., it will work on just about any carrier.
How to choose
Get the right specs
Why you can trust Android Central

Samsung phones are updated every year, and while long-term software support and quality hardware means you don't need to upgrade your phone annually, there are often worthwhile upgrades to entice you to pass on your old one and grab something new. Samsung has even started giving its mid-range phones like the Galaxy S25 FE, seven years of Android upgrades.
As of now, the Galaxy S25 Ultra is the best Samsung phone of 2025, primarily due to its sophisticated blend of super-powered hardware and impressive software features. The 120Hz AMOLED display is sublime, the internal hardware is the fastest of any phone today, and the 200MP camera outclasses most other sensors without trying.
Premium specs often come at a premium price, so the S25 Ultra may not be the best choice for everyone. If you're working with a smaller budget, the base model Galaxy S25 is almost just as good. The S25 boasts a vibrant 120Hz screen with a compact 6.2-inch construction, while the Snapdragon 8 Elite for Galaxy processor — when paired with the 4,000mAh battery — makes the phone run smoother and more efficiently than any base model Galaxy phone to date.
On the more affordable end, Samsung offers the Galaxy A55 5G with hints of the flagship Galaxy S models trickled down to a mid-range price that can be incredibly appealing if you can't push your budget as high as the S25 models. The Galaxy A55 finally switches to a metal and glass build, has a 120Hz AMOLED screen, 5G connectivity, and comes with a promise of four Android OS upgrades.
The Galaxy A35 is also worth a look as it's nearly identical to the A55 and is cheaper, but you should only choose that if you don't care much about mediocre cameras and performance.
If you're into the flip and foldable style phones, the Samsung Galaxy Z Flip 7 and Galaxy Z Fold 67cost more but will be conversation starters. Please, they're all just downright cool.
Should you wait for the Samsung Galaxy Z TriFold?

Samsung put the rumors and leaks to rest on Dec. 1, 2025 when it confirmed the Galaxy Z TriFold, a phone that folds twice and has an inner screen with three sections. The phone will release in South Korea on Dec. 12, and is set to eventually launch in other markets. These include China, Taiwan, Singapore, the UAE, and the U.S., but a release date more specific than Q1 2026 has not been set.
It may be worth waiting for the Galaxy Z TriFold if you're wanting a true tablet-sized device that can fold up and fit into your pocket. However, it won't be cheap. The Galaxy Z TriFold's pricing isn't official, but we expect it to retail for close to $3,000 in the U.S. "Galaxy Z TriFold will be available in the U.S. in the first quarter of 2026 with more details to be shared later," according to Samsung's newsroom post.
If the Samsung Galaxy Z Fold 7 doesn't provide enough screen real estate for your needs, perhaps it's worth waiting for the Galaxy Z TriFold.
Should you pick a Samsung over an iPhone?

When you compare a Samsung Galaxy phone to an Apple iPhone, we think there's no real contest. While Apple's products have plenty of positive traits — including great customer service at physical Apple Stores — Samsung's phones are feature-rich and often feel a step ahead in terms of technology.
From a physical design standpoint, Samsung phones usually sport bigger screens with smaller bezels around the edges, sleek designs, and sometimes even extra special features like the S Pen built into phones like the Galaxy S25 Ultra. Samsung's displays are world-class and are the brightest you'll find in any phone. There's a reason even Apple uses Samsung displays in its phones.
On top of that, Samsung has been leading the pack in innovation, with devices like the Galaxy Z Fold 7 and Galaxy Z Flip 7, which offer large and impressive foldable glass displays in pocket-friendly form factors.
On the software front, Samsung offers great long-term support for its flagship Galaxy S phones, affordable Galaxy A phones, and its folding phones. The flagships get seven years of support while the more affordable models still get a very competitive four years. We're talking years of support, and optional add-ons like Samsung Care+ are often better than insurance offered through your carrier of choice. Plus, Samsung's AI features keep getting better and are trickling down to lower models too.
Samsung phones ship with a bevy of options that cater to every kind of user, from beginners to power users. And optional downloads like Samsung Good Lock offer customization options that Apple users could only dream of, including plenty of features that most other Android phones don't offer either.
Samsung phones are powered by Android — that's the world's most popular operating system if you didn't know — which means they are compatible with a dizzying array of great accessories and smart products in every category imaginable. Since most smartphones are powered by Android, you could always pick a different non-Apple brand of phone the next time you upgrade and you won't lose access to apps or services you already enjoy on Samsung phones.
Do Samsung phones come with a charger?

Most Samsung phones do not come with chargers these days. Samsung has been making the decision to ship without chargers on a piecemeal basis, typically foregoing them in an effort to become more environmentally friendly and avoid adding e-waste to landfills, as the company previously stated.
Unfortunately, the lack of a charger in the box doesn't mean phone prices have dropped at all. Samsung — and a number of other companies — say that users continue to re-use old chargers and often don't even take new chargers out of the box. Other users pick up great wireless chargers to use in place of traditional wired chargers.
Most premium Samsung phones use 45W charging, further negating the need for a new charger to be included in the box. Chance is, if you've got a charger at home already, it's probably no better than a new one that would be included in the box anyway. Thanks to USB-C, however, chances are you have dozens of them lying around that can power Samsung phones.
Do Samsung phones support microSD cards?

SD card support is one of the many casualties of modern smartphone design. Along with 3.5mm headphone jacks, IR blasters, and removable batteries, SD cards have become less and less common. No Samsung flagship phone in 2025 — that means phones that normally cost $800 or more — supports removable SD card storage.
While there could be many legitimate reasons for removing SD card support, two of the biggest are the inclusion of more internal storage and the proliferation of cloud storage. Services like Google Photos can automatically back up your photos and videos, keeping your internal storage free for other apps and games, and many phones ship with at least 128GB of internal storage these days.
But one of the many bright sides of saving a bit of cash on a phone is that, more often than not, budget-friendly phones include budget-friendly features like a 3.5mm headphone jack and removable SD card support. That includes many of the Galaxy A series, like the Galaxy A15, A25, and A35. This means you won't need to spend a bunch of money on expensive internal storage when the best microSD cards only cost a few bucks.
Do Samsung phones support eSIM?

Most modern Samsung phones support eSIM but don't do away with the SIM card tray. That means, on phones like the Galaxy S25, Z Flip 7, Z Fold 7, and even some Galaxy A-series support eSIM.
There are many advantages of having the option to use both eSIM and a physical SIM at the same time. Folks who travel a lot can use multiple carriers that offer better pricing or cell services in different locations. If you have no desire to juggle between more than one carrier, using the same carrier for both eSIM and a physical SIM can increase network bandwidth, offering a way for power users to get better upload and download speeds without having to do much at all.
As usual, the best part of a Samsung phone is the choices offered to users. It's something for everyone!
Get the latest news from Android Central, your trusted companion in the world of Android

Harish Jonnalagadda is Android Central's Senior Editor overseeing mobile coverage. In his current role, he leads the site's coverage of Chinese phone brands, networking products, and AV gear. He has been testing phones for over a decade, and has extensive experience in mobile hardware and the global semiconductor industry. Contact him on Twitter at @chunkynerd.
- Roydon CerejoContributor
- Brady SnyderContributor
- Namerah Saud FatmiSenior Editor — Accessories
- Michael L HicksSenior Editor, Wearables & AR/VR
