Security

Your phone is your life. It's got your contacts. Your pictures. Your emails. Your text messages. Things you wouldn't want just laying around in public. And, more and more, your phone contains your company's secrets. Who your company does business with. Strategies. Financial information. Or, perhaps more important, customers' private information.
You need to keep your Android phone safe and secure. We can help.
The good news is we've got more tools than ever at our disposal should something bad happen to your phone or tablet. There's absolutely no reason for you to lose data anymore. Nor is there any reason for you to fear the security of your data should your phone be lost or stolen. And if you're using your phone for work as well as personal business, there's no reason why your company should have to worry that its data is secure.
There are plenty of options.
For personal use, you've got to start by putting a lock code on your phone. Be it a simple PIN, pattern, password or facial recognition, you simply can't afford to have your business spread out where anyone can see it. (In fact, stop what you're doing and check your phone. If you don't have a lock code on it, here's how to add one.) But that's only half the battle. We recommend using a password manager that helps you create and store unrecognizable passwords — gibberish, really — to keep scammers from simply guessing their way in. And then we demand that you start using two-step authentication — a password and a unique, one-time code sent to your phone — for your most trusted accounts. That means Google. That means Facebook. That means Twitter.
You simply can't afford to.
For businesses, you've got things like Samsung's SAFE and KNOX, which help provide walled gardens for apps or data, under company control and completely separate from your personal stuff. That means your stuff is yours, their stuff is theirs, and never the twain shall meet, all on one device. And there are other options, too, from many other providers.
It's an old wives' tale that Android isn't secure. It's only not secure if you don't bother to make it secure. And we'll help you through it.
Latest about Security

These are the most secure Android phones that you can buy today
By Jerry Hildenbrand last updated
Safe & sound With one of these secure Android phones, you don't have to worry about the safety of your data. These phones have great hardware, cameras, and more.

Android now warns before you open banking apps during risky calls
By Sanuj Bhatia published
In-call safety arrives Google expands in-call scam protection to the US, warning users that opening financial apps during a call could expose sensitive data.
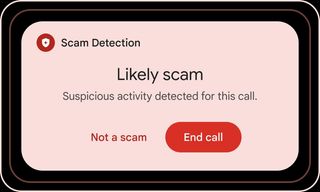
Google takes legal action against major phishing network targeting millions
By Nandika Ravi published
Shields up! In a bold legal maneuver, Google is targeting the notorious "Lighthouse" phishing operation, impacting over one million victims globally.

Google says Android phones now block more scams than iPhones
By Sanuj Bhatia published
Google takes the lead Android's AI-powered detection reportedly outperforms Apple's tools, blocking 10B scam messages and 100M suspicious numbers.

Flaw in OnePlus phones lets apps read your texts, fix rolling out soon
By Jay Bonggolto published
Patch incoming OnePlus breaks silence and promises fix for SMS bug.

Is fingerprint security really safe? Here are the risks, benefits, and alternatives
By Jerry Hildenbrand published
Ask Jerry Have a question about the tech in your life? If so, maybe we can get them answered!
How to enable sensitive content warnings in Google Messages
By Sanuj Bhatia published
Protect your inbox Google Messages uses on-device AI to warn you before opening harmful or unwanted images.

How secure is Bluetooth pairing on the Galaxy S25?
By Derrek Lee last updated
Bluetooth security If you own a Galaxy S25, you're likely pairing multiple Bluetooth devices to it. How secure is your Bluetooth connection?

How well does the Galaxy S25 detect fake fingerprints or facial data?
By Derrek Lee published
Biometrics The Galaxy S25 features a fingerprint sensor and face unlock, but are they secure?

The balance between easy and secure is tough, but your finger is the answer
By Jerry Hildenbrand published
Who are you? Adding more authentication is good, as long as it doesn't get in the way.

Android users to finally get an extra layer of security on Chrome
By Sanuj Bhatia published
Safer autofill Chrome will soon ask for biometric verification before autofilling passwords on Android.

Google is taking the hackers to court over a major Android fraud ring
By Jay Bonggolto published
Malware in the box Google is taking legal aim at the minds behind BadBox 2.0, the botnet that quietly crept into 10 million knockoff Android devices.

Every COROS watch has a major vulnerability exposing your private data
By Michael L Hicks last updated
Not good A major Garmin watch rival has acknowledged the breach, which gives hijackers access to all the data on your watch, including notifications.

How to enable Advanced Protection on a Google Pixel phone
By Christine Persaud published
Keep it ironclad Advanced Protection is here to keep your Pixel phone safe. Here's how to enable it.
Wonder what life is like without Google or Apple? You need to try this alternative
By Jerry Hildenbrand published
The real deal Open-source software for your phone has been around for a long time. It's never been done this professionally before and you owe it to yourself to have a look.

Ask Jerry: How can I securely wipe a phone?
By Jerry Hildenbrand published
Ask Jerry Have a question about the tech in your life? If so, maybe we can get them answered!

Tech Talk: What you need to know about crossing the US border with your phone
By Jerry Hildenbrand published
Tech Talk Breaking tech down to its simple parts so we can all understand it a little better

Google is trying, but authentication is still terrible
By Jerry Hildenbrand published
WHO AM I? We need to prove we are who we say we are, but we want it to be more streamlined.
Get the latest news from Android Central, your trusted companion in the world of Android


