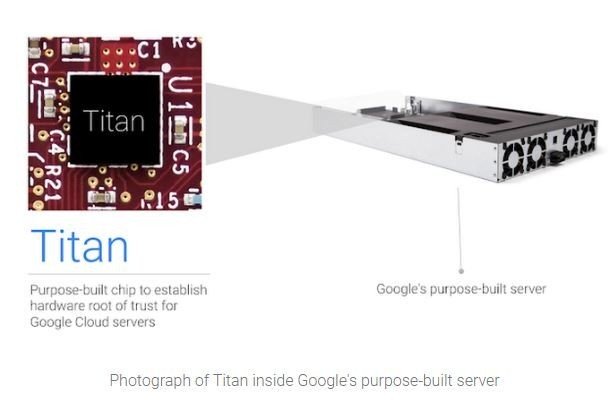
What is the Titan Security Module?

You might have heard about Google's Titan security chain. It's an idea that started for use in servers, then moved to security key fobs used as two-factor authentication devices, and with the Pixel 3, ended up inside a phone.
The simple explanation is that Titan is the name of the chip that lives outside of any processor and things like logins and encryption/decryption are funneled through it. But there are plenty of differences between the three versions, and that's what makes everything work together — they're specialized for their particular use-case.
It's interesting enough to talk about how it all works, so that's what we're going to do here.
Server-Side Security
You might not know it, but Google designs and custom builds many of the servers it uses. It designs the hardware, uses a firmware-stack that Google controls, its own hardened hypervisor and even a Google-curated operating system. Beyond that, the physical security on the buildings themselves is tightly controlled.
Part of the hardware-based root of trust Google has is the Titan chip. It's used in two different ways to make sure your data, as well as almost every part of Google's Cloud Platform, is as secure as it can be: Secure Boot and Cryptographic identity.
The first thing Titan does is make sure the server software is what Google says it should be.
Most computers boot the same way. There are some baseboard management controllers that have their own firmware that gets the party started, then the CPU loads a boot firmware image. Once the bootloader is loaded it takes over and loads an operating system.
A Secure Boot process depends on a couple of things: an authenticated boot firmware image and bootloader process and a digitally signed copy of the operating system files. Your phone does this, your laptop or desktop do this, and most servers do this. Google adds the Titan chip into the mix to harden the process.
Get the latest news from Android Central, your trusted companion in the world of Android
Titan acts as the secure element in the boot chain but it also does it in a pretty unique way. Because of the hardware inside the Titan module — which is completely isolated with its own processor and memory — it can start monitoring the boot process as soon as the board controllers get started. Titan first runs a self-check of its own firmware, then every byte of the normal booting process is monitored in real-time. When the server is booted, there's no way something sneaky found its way in.
The Titan module is also the heart of a server's cryptographic identity.
Titan on the server also is the main part of an end-to-end cryptographic identity verification process. Each chip has its own unique key and they all communicate through a Titan Certification Authority that verifies each and every chip is running the correct firmware and even controls system logging so nothing can happen without a proper record.
When you've established a link to data stored on a Google server, all encryption and decryption requests go through the Titan module to make sure you are you, make sure you have the authority to access the stored data you requested and to make sure the entire server is secure without any rogue services or application processes in play.
Google takes server security very seriously because if it didn't it would soon go out of business. Titan started on servers because of this, and it's an awesome way to protect not just our data but all the data used by any Google Cloud Compute process.
Two-factor authentication

The next step for the Titan chip was to shrink it down and use it for a two-factor security key. Not just any key though, as Titan Keys are FIDO compliant keys that prevent users from falling for a phishing attack.
What that means is that the Titan M chip inside the key fob checks that it's running the firmware that it should be when it's electrically activated, then it's used as an authentication device.
Two-factor authentication: Everything you need to know
FIDO protocols are used to prevent phishing attacks using public-key cryptography. Most browsers are FIDO compliant and many work with hardware-based 2FA like a security key. When you open Chrome and create an account at a website, a FIDO compliant key can be used to build a public/private key pair on both your device and the web host. Public keys are exchanged, and the next time you visit you can authenticate using the same device used to register.
FIDO services and keys make sure you don't get phished.
If a "fake" site is built to try and phish your account, the private key from the host won't be able to pass the security challenge and you are unable to log in. This means someone can't phish your username and password.
There are a lot of FIDO compliant keys out there, but the Titan chip on Google's is there to make sure that the tiny bit of code that runs on a security key is the right bit of code every time you use it.
Titan on your Pixel
With the debut of the Pixel 3, the Titan M chip is now inside every Pixel going forward.
This means you get all the benefit of using a physical Titan security key and instead of digging it out of your pocket and plugging it in to authenticate, unlocking your phone authenticates it and keeps it active.
Now you don't need a little fob if you buy a Pixel.
When you use a Pixel with a Titan M chip to sign up or access a secured website, like your Google account controls or Amazon or any other FIDO compliant web service, you're protected from phishing just as if you used the actual Titan key fob.
The Titan M chip inside your Pixel also works during the cryptographic process and acts as a secure boot controller as we see on Google's actual servers. You can turn off the requirement, but with it enabled the Titan chip checks the digital signature of the boot image and monitors the process, halting if something isn't what it should be.
It also verifies encryption/decryption keys for data moving in and out of your Pixel phone so the whole process can be faster and safer at the same time. When you're communicating with a Google server for something like a backup or restore operation, two Titan chips working together mean your data is about as safe as it can be. And that's been independently verified and found to be true.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.