Lockdown: How secure is your smartphone? - Talk Mobile

Presented by Blackberry
Talk Mobile Gaming
Lockdown: How secure is your smartphone?
by Rene Ritchie, Daniel Rubino, Kevin Michaluk, Phil Nickinson
Look at your smartphone. You likely have at least one email account on it, along with the associated contacts and calendar. You have your memos and to-do list. There's your browsing history. Your phone history and text messages. Years of photos. Probably Facebook, and maybe Twitter or Google+. You might have a banking app, stores you frequent, or a travel app with your airline tickets.
More and more of our lives are on our smartphones and tablets. These tools have become increasingly useful, but that makes them increasingly problematic. Your digital life resides on and can be accessed through this device. This personal disposition makes our phones a mine of data about us, some of it potentially incredibly sensitive and damaging.
These phones track us everywhere we go - what apps deserve access to that data? Can we trust our smartphones to make financial transactions with businesses and our friends? How do we keep everything on our phones secure, and what do we do if we lose it? And what about everybody else's personal social network and contact data on that device?
The more that's on your phone, the more important security becomes.
Get the latest news from Android Central, your trusted companion in the world of Android
Let's get the conversation started!





Security
Articles navigation
- Location security
- Video: Michael Singer
- Mobile payments
- Device security
- Video: Sebastien Marineau-Mes
- Outside data
- Comments
- To top

Phil Nickinson ANDROID CENTRAL
Where you are, where you've been, where you're going
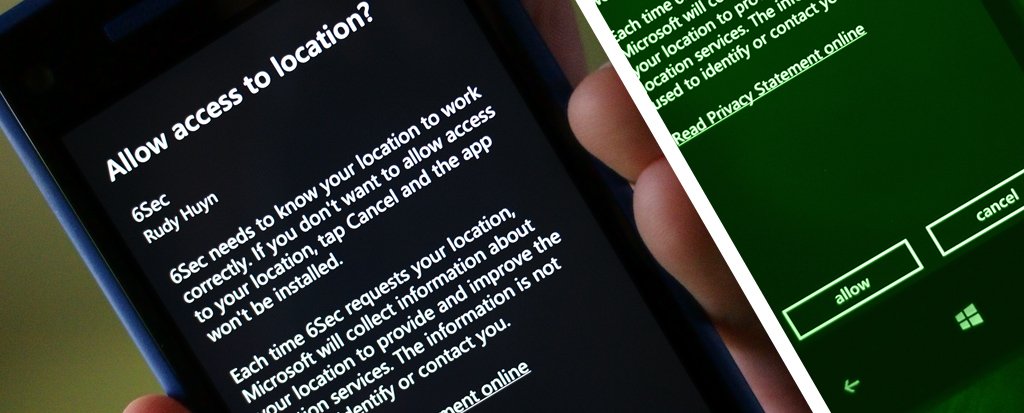
We give out our location every day. Many times a day. In many ways. Our mobile devices basically have become beacons for where we are, where we've been — and, more recently, as an indicator of where we're going. This is by design, of course. And like any new technology, it's good and bad.
GPS isn't the only way to get a fix on your location. It's not just for maps. Any application can get a GPS fix, whether that's necessary for the app or not. Moreover, there are secondary systems that can figure out where you are as well. Maybe not with the same degree of accuracy, but still close enough.
Cellular systems know where you are. Wi-Fi triangulation can build a disturbingly accurate location profile. Or, flipping that coin over, they can provide quicker and more efficient location data. And it's getting better all the time. That's where we're at now.
Welcome home, Mr. Savage
On February 9th, 2010, host of Discovery Channel's MythBusters posted a photo on Twitter of his truck, parked in front of his house, with the caption, "Now it's off to work." What did the photo reveal? The Savage drives an old Toyota Land Cruiser, that he was leaving his house, and the exact GPS coordinates of his front door.
Having neglected to disable the geotagging function on his iPhone, Savage had inadvertently posted his home address in the form of his location coordinates in the photo's metadata. He claimed to have known about geotags, but that, "I guess it was a lack of concern because I'm not nearly famous enough to be stalked. And if I am, I want a raise."
Celebrities aren't the only ones who have to worry about geotagging giving away too much info. Posting a photo of your new TV? If it includes geotags, you could be posting your address for enterprising burglars. Geotags are great for when you want to declare where you are - not so much for when you don't but still want to share a photo.
Protecting your location data — that is, turning everything off, all the time — isn't impossible. But it's not all that easy, or convenient. We trade privacy for convenience every day. At the very least, we'd argue that it's more important to be educated about how, when and why your location data is being used, than to panic and turn it all off. It has benefits.
We trade privacy for convenience every day.
Start with the simplest: Know how to turn off GPS on your phone. Know how to turn off the secondary locating systems. The good news is that the operating systems have gotten very good at being upfront about all this. You should have been asked for permission the first time you used your phone (or, in some cases, the first time you used an application). Location settings should be and usually are pretty clearly marked in your phone's settings app.
Also know how to turn off GPS tagging on photos. It's a great service for things like vacation shots — or anything else that could benefit from knowing when and where the picture was taken; it's so much better than writing on the back of a printed 3-by-5 photo — but maybe not the greatest idea if you're posting pictures from your home.

A few years back, if I got something that looked suspicious, I'd actually open it on my mobile, thinking, well, it probably won't hurt my mobile.
- Michael Singer / AVP Mobile, Cloud and Access Management Security
Q:
Do you worry about the security of your location data?
876 comments


Daniel Rubino WINDOWS PHONE CENTRAL
Your smartphone, your wallet - one and the same
In 2013, we have seen the rise of financial transactions from mobile devices. Whether it is something as simple as sending funds via PayPal, or something more elaborate like scanning checks via your smartphone for bank deposits, never before has money so freely been transferred digitally.
It can be a scary thing. After all, one wrong decimal place, one bug in some software could seemingly clear out your account. When money is "only digital", that is a risk. Then again, that's a risk when writing a check - put too many zeroes on that slip of paper and you'll be in a bad place real quick.

A maze of mobile payments
The concept of 'mobile payments' is relatively new and has taken on many forms. There hasn't even been yet an agreed upon standard for how to take mobile payments, with services and retailers supporting an array of options, including optical scanning of on-screen bar codes or QR codes, text messages, payment through an app, and NFC transfers.
In the United States, the largest mobile payment system belongs to none other than Starbucks. The Seattle-based coffee shop chain has more than 7,000 locations, with most supporting scans of bar codes displayed by their mobile apps for payment, tying into a web-based account manager.
Globally, the biggest mobile payment network can be found in Kenya. The M-Pesa mobile banking service is used by more than 17 million Kenyans. M-Pesa works without requiring access to a physical banking location, and users can deposit or withdraw money from their accounts, pay bills, and transfer money to other M-Pesa users.
There are risks, sure, but they're a trade-off for increased convenience. Paying via NFC or sending a payment wirelessly is very enticing for the consumer on the go. Sure, cash is always more secure than credit or digital, but how often do you carry analog money these days? How many slips of paper and metal discs do you want to carry around with you? There's not much more antediluvian than seeing a store or service that doesn't take credit or PayPal.
And that's not even considering the security of credit and mobile versus cash. If your phone is stolen, you can remotely wipe it. If your credit card is stolen, a quick call to the bank will cancel it and any charges on it. If your wallet or purse full of cash is purloined, that money is gone and it's never coming back.
Just how secure are mobile payment systems? Banks invest a lot of money into their security to prevent such potential hacking and cellular encryption technologies have made it far more difficult for casual criminals to "sniff" out passwords or information by listening to radio traffic. But as the recent NSA scandal in the United States has shown, no system is foolproof, especially if the organizations involved hand over the keys.
No system is foolproof, especially if you hand over the keys.
Again, tradeoffs. If you go with digital, you are placing yourself firmly on "the grid", with the ability to be tracked, monitored and even hacked. Want to avoid that? Then go off the grid and back cash money, while giving up convenience. The choice, as always, is yours. Just know that it's really hard to buy that leg lamp off eBay with cash.
Q:
Are you comfortable making payments with your phone?
876 comments


Kevin Michaluk CrackBerry
Phone lockdown: passwords, pursuits, and permissions
What's the best way to secure our data on mobile? Buy a BlackBerry! I kid. Kind of. Not really. If there's one mobile manufacturer with security woven into their DNA, it's BlackBerry. Their prominence in governments and corporations is due to that security. The President of the United States uses a BlackBerry because of the security. And maybe the keyboard.
When it comes to protecting yourself, there are steps you can take to protect your device and - more importantly - the data on it.
Something, anything, that puts a layer of authentication between the power button and your stuff.
Step one: Password protection. Use a pin lock or pattern lock or even Android's silly face unlock. Something, anything, that puts a layer of authentication between the power button and your stuff. If you leave your phone behind and it isn't password-protected, whoever picks it up has instant access to nearly everything on your phone.
You're probably permanently logged in to social networks, your email, your cloud storage, your memos, and everything else. If anybody who picks up your unsecured phone has access to everything, you'll be in a world of hurt.
Password protect your phone. It's a minor inconvenience, but worth it.
On the subject of passwords, make them strong. Use numbers numbers, letters (upper and lowercase), and special characters. Never reuse passwords - if one site's user records are leaked, your data elsewhere could be exposed.
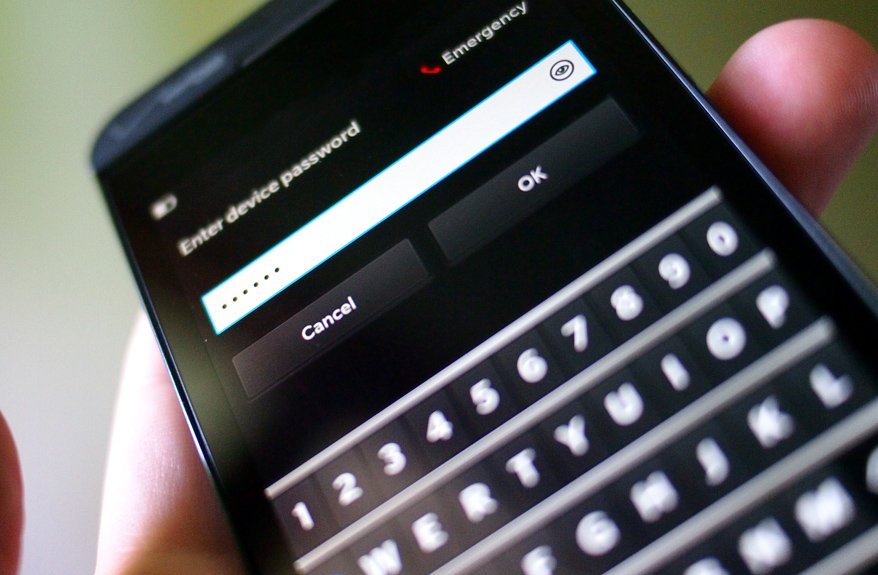
10^4
Chances are you don't share the same PIN lock code as somebody else you know (unless it's something like 1234, 0000, or 2580). The typical PIN code is just four characters, which yields just 10,000 possible combinations. So, chances are that somebody else has the same code as you. A couple thousand somebody elses.
A machine unveiled in 2013 named the "Robotic Reconfigurable Button Basher" is capable of trying all of those 10,000 possible combinations, and won't fatigue while doing so. The machine is with three cheap motors, a microcontroller, and a webcam - all hooked up to a cheap PC. It keys in PIN codes until its had its way with the phone. Able to try a new code every second, and only deterred by a 30-second time-out period after five incorrect tries, the R2B2 can try every possible combination in just 20 hours.
Step two: Enable lost phone tracking. BlackBerry, Windows Phone, and iPhone all have this, and while Android inconceivably does not on an OS level, there are third party options. If you lose track of your phone, these can tell you where it is and trigger an audible alarm so you can find it. If it's beyond your reach, it can remotely lock and wipe it.
Step three: Be mindful of app permissions. It sounds fear-mongering, but be especially aware on Android. Google Play scans apps for known malware, but there's no verifying that they're requesting legitimate access. Thankfully, Google Play does tell you what permissions the app requests before you download. Make sure the permissions the app requests make sense.
Step four: Use common sense. The more you put yourself "out there", the more you're exposed to attack. Public records, data dumps, and just scanning what's on your social networks can reveal a lot about your identity.
The unscrupulous types that trawl the internet look for easy targets. Don't be low-hanging fruit.

Security has to be built into the architecture.
- Sebastien Marineau-Mes / Senior Vice President, BlackBerry OS
Q:
How do you keep your phone secured?
876 comments


Rene Ritchie iMore
It's not just your information on that smartphone
Our own data leaks are bad enough. Never mind when Facebook or Amazon or some other giant internet company accidentally opens our kimonos and exposes our stuff to one and all. When our friends' data leaks, it's even more maddening. Maybe it's a rogue app sucking up our contacts, a DM we sent as a public reply, or just a nosy fellow commuter peeking at our screen, but in some ways it feels like we're only ever a moment away from letting down those we love the most.
There's always the Battlestar Galactica approach -- keep everything wired down and offline. But that's not realistic, especially on mobile devices like phones and tablets. So what can we do?
First, we can decide which data-driven services we really need. Not all social networks actually provide value in exchange for the information they suck down. If you stop using something, don't just leave it to wither, go turn it off. Cancel your account and kill it dead, so that if the derelict service is ever hacked, or even sold, it no longer (legally) has your stuff.
Say please...
After high-profile scares of apps surreptitiously accessing unrelated data without telling the user, mobile platforms have instituted clear permissions standards to prevent further shenanigans. On iOS, apps must request permission to get a user's location, or view their calendar, contacts, reminders, or photo. iOS 7 will add a requirement for microphone access as well.
Android allows for micro-managing of permissions, and the Google Play store presents users with a list of requested permissions before purchasing. Permissions include making phone calls and sending text messages, reading contacts and calendars, phone state, location, and even network access to, well, download things. Android apps can also have permissions for cross-app data access.
Microsoft too allows for low-level permissions viewing, including calendar, camera, contacts, location, orientation, photos, microphone, network awareness, push notifications, and the device's web browser, among others. BlackBerry 10 requires permissions to access background processing, messages and emails, the camera, contacts, location, microphones, notifications, the phone, shared files, and more.
Next, don't give anything access to stuff it doesn't really need access to. Most operating systems are smart enough to ask your permission before granting access to your contacts. Don't give it unless you really need to, and think about turning it off once you've done what you need. Likewise, social apps that want access to your messages or timelines or anything else. The moment they're not providing something you urgently need, kill their permissions, and their potential to cause you and your friends problems.
If they're not providing something you need, kill their permissions.
Once the system is as locked down as you can make it, the rest is up to you. Be discreet. Don't play voicemails out loud in public (that's just rude). Don't enable set up your phone to show your friends' private pictures on your home screen. Don't leave your phone unattended on a bar or restaurant table.
And most importantly, use strong passwords, and different passwords for every site for which you register. That way, if one is compromised, the others are still safe. That's not just a best practice for your data, but for the data your friends have knowingly or unknowingly entrusted to you.
Q:
Talk Mobile Survey: The state of mobile security
Conclusion
With so much data on our mobile devices, and so much of it so frighteningly sensitive, but keeping it all secure isn't as insurmountable of a prospect as it might initially seem. A few simple steps can go a long way towards making a difference.
First and foremost, we have to secure our devices. That means password or pin locks, lost phone tracking services, and being aware of which data permissions we're granting to which apps. After all, everything from our email and calendar to our friends' contact information and our own banking info can be found on these devices. It might look relatively benign sitting there on the table, but in the wrong hands it can be a disaster.
We also have to be mindful of what we put online. Use common sense when posting your personal information online, even if it seems inconsequential. Consider whether or not you want or need geotagging for your photos, or which apps have reason to know where you are. Don't reuse passwords on different sites, don't leave your phone unattended, and just use common sense.
What can we do to stay secure when mobile?