FUD fighting: Every smart device has unpatched vulnerabilities
OMG! Have you heard? Half of all Android devices have unpatched vulnerabilities, and are out there, sharing the same air as we are! The horror!
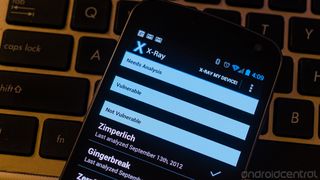
That's the feeling you'll get if you poke around the Internet today and read a blog or two, where folks are talking about a study from Duo Security, a company that sells authentication software to be used on smartphones. They even have a nifty little app you can install to check your Android device to see if it's vulnerable. The app isn't in Google Play, but it's linked at the bottom of the post if you want to check it out yourself.
Sounds scary, right? That's 50 percent of Android phones, all over the world, all unpatched and ripe for some sort of online hacking has got to be bad. It's the end for Google and Android, and we're all screwed.
Just. Stop.
Here's what's going on. The app you can download runs and scans your device to see if any of eight popular root exploit holes are still open. These are things that were patched in more recent versions of Android or newer versions of the Linux kernel. If your phone or tablet is unpatched, you'll get a warning about it. It's all above-the-board, and these exploits probably are unpatched in 50 percent of Android phones.
But what about the other thousands of exploits, or the ones that haven't been made public yet? You can't just use the eight easy ones and call it a day. My Galaxy Nexus is safe, according to this app, but it's sitting there with an unlocked bootloader, rooted, and ready for bad things to happen. You're not getting the full story from this app -- or from the blogs out there talking about it.
But we can help.
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android
Every piece of smart electronics you own is unpatched against vulnerabilities. Every single one. Probably more than one vulnerability as well. That means your Android phone, or your iPhone, or your laptop, or even your DVD player. There is no way to create software that can't be exploited, and we see that daily. The 256-bit AES encryption on a bootloader means you'll have to find another hole and exploit it another way. There are people out there smarter that you and me who will find a way to crack into anything with a user interface as long as it's popular enough to care about.
That doesn't mean device manufacturers get a pass, though. If Google can make the Galaxy Nexus safe from popular exploits, that means that Samsung, HTC, Motorola and the rest can do it as well. If you want to provide a device with your own software on it, you're responsible to maintain that software for the reasonable life of that device. For us, that means at least for the warranty period or the length of any contract we may have signed with a carrier. If you can't do that, you have no business putting your own custom software on a device.
But for this current round of Android hate, feel free to quietly chuckle and nod. FUD happens, but your phone is as safe as your cable box, and unless you're doing something you probably shouldn't be you won't have any issues.
Source: Duo Security; via BGR

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Twitter.
