Why Android security fearmongering is total BS

Get the latest news from Android Central, your trusted companion in the world of Android
You are now subscribed
Your newsletter sign-up was successful
There's been plenty of FUD — fear, uncertainty and doubt — spread surrounding Android phone security over the years. And I'll be honest: in the early days, much of it was well deserved. The fragmented nature of Android, the sheer amount of stuff that required a full firmware upgrade in order to change, and the reticence of phone makers to roll out those updates meant that Android phones were more susceptible to security issues than the iPhone.
Ten years ago if a major iPhone security vulnerability was discovered, Apple could quickly patch its entire ecosystem. On Android you could be left waiting months, if a fix ever made it to your device. For an Android security issue to be addressed in 2011, new code first had to be pushed out by Google, then integrated into your phone's firmware by the manufacturer and eventually signed off by your carrier. That's not an ideal sequence of events if time is of the essence, as it likely would be if a nasty new software vulnerability were being exploited in the wild.
Android security has come a long, long way in the past 10 years.
But Android in general, and Android security in particular, has come a long way over the past decade. And the tired trope of Android owners never getting updates, and Android phones being mired in malware is now well and truly outdated. The best Android phones now guarantee four years of regular security patches, and Android itself is now more secure by design.
The problem is, the ways in which Google keeps Android safe and secure are nebulous and pretty technical. While Apple, with its vertical integration and relatively small number of phone models, can simply roll out full firmware updates at will, Google's larger, more diverse and less directly controlled ecosystem requires a different approach.
Google Play Services

Pretty much every Android phone sold in the West comes with Google Play Services — it's an important part of the package of mobile apps preloaded onto Google Android phones, and it can be silently updated by Google in the background. But Play Services is far, far more powerful than your average Android app. That's because it's a system app, which basically means has the keys to the castle, allowing for features like remote wipe of your phone if it's lost or stolen. (For that reason, system apps have to first be loaded onto the device by your manufacturer. They can't be installed from scratch like a normal app.)
Current versions of Google Play Services are supported all the way back to Android 5.0 Lollipop, released in 2014. The last version of Android to lose Play Services support was 4.0 Ice Cream Sandwich, released in 2011, which was retired in 2018. That means for "current" Google Play Services support, the timeframes we're talking about here are a lot longer than most people will ever keep a smartphone.
More: A Google Mobile Services primer
Get the latest news from Android Central, your trusted companion in the world of Android
Play Services also does a whole lot of other things, like allowing developers to integrate services like Google Pay and Google single sign-on into their apps. But let's zero in on the security implications: This kind of system app, constantly kept up-to-date in the background, supported on devices released seven or more years ago, and with permission to do basically anything, is a powerful tool in Google's Android security arsenal.

Play Services is always up-to-date even on ancient Android phones, protecting against malware.
Google Play Protect, for instance, is part of Play Services. This lets Google check the apps on your phone for malware, whether or not they're downloaded from the Play Store. Because Play Services is a system app, Play Protect can nuke malicious apps before they have a chance to do any harm. And because Play Services is constantly updated, these defenses can be kept up to date in the background many years after your device receives its last proper firmware update. It's a way for older devices to be protected against malicious apps, even if those apps use software vulnerabilities that are still technically present in the underlying OS.
It's this which can give devices like the now geriatric Samsung Galaxy S4, released in 2013, a decent level of protection against vulnerabilities present in its Android 5-based firmware.
A great example of the power of Google Play Services can be seen in the Covid-19 Exposure Notification System. Google was able to build this system with Apple and, thanks to Play Services, automatically deploy it to every Android phone running 5.0 Lollipop or above without updating their firmware.
When scary software vulnerabilities emerge, as happened in 2014 with the "Fake ID" bug, Google immediately updated its "Verify Apps" feature (a precursor to Google Play Protect) to identify offending apps. This allowed the vulnerability to be nipped in the bud long before manufacturers got around to rolling out firmware updates addressing the underlying bug.
But of course, not having vulnerabilities in the first place is better than just preventing them from being exploited. To that end, in recent years Google has tackled Android's long-standing firmware update problem in several different ways: Firstly, by making Android more modular, and working more closely with manufacturers during Android's development. And secondly, by clearly tying a date to Android's level of security, and writing minimum support requirements into its contracts with phone makers.
Android goes modular

A decade ago, Android was a big monolithic entity that had to be updated all at once. Changes to system-level things like media codecs or networking — or even the built-in web browser or dialer app — could only be done via a full firmware update, with all the hassle that entails. (First, Google pushes new code out, then the manufacturer turns it into a device-specific firmware update, then the carrier has to sign off.) And as mentioned earlier, that's slow and pretty bad for security if an exploitable bug is discovered.
In the years since then, Google has made Android more modular, making it quicker and easier for companies to push out OS updates. And more recently, it's now possible to update chunks of the Android OS without a full firmware upgrade. All of this makes it possible for Google and phone manufacturers to respond fast to fix security issues in certain parts of the OS.
Google's earliest steps in this direction involved breaking certain apps and components out of the firmware and allowing them to be updated via the Google Play Store. The best examples of this are Google Chrome and the Android WebView component — used for web content inside Android apps. Updating these independently of the firmware lets Google fix browser engine bugs that could be exploited by malicious web pages, and get them rolled out to the entire Android ecosystem in hours instead of months.
Recent versions of Android get rid of the update middleman.
In 2017's Android 8.0 Oreo release, Google stepped things up a gear with "Project Treble." This was an effort to disentangle the low-level bits of Android from chipset manufacturers like Qualcomm from the rest of the operating system, and create a more modular OS that could be updated more quickly. With hardware companies able to separate out their own customizations from the core OS, the idea was that firmware updates could be pushed out at a more rapid pace and with less technical legwork. Project Treble isn't something you'll notice running on your device, but it could be the reason why the Android phone you bought in 2018 got OS updates quicker than the one you purchased in 2016. And quicker updates, of course, are better for security.
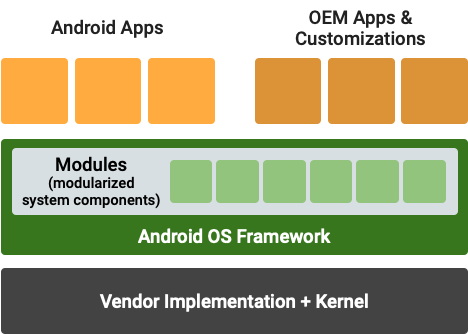
The next step in modularizing Android came in Android 10, with "Project Mainline" — known today as the vaguely named "Google Play System Updates." Mainline is all about sidestepping the existing over-the-air firmware process entirely and bundling parts of Android into new modules which could be updated directly by Google or your phone's manufacturer. Mainline grew in Android 11 with updateable modules for more Android system bits like Wi-Fi, tethering and neural networking components. And in Android 12 it'll also cover ART (the Android runtime), bringing more security benefits. As AC's Jerry Hildenbrand explains in a recent editorial:
In Android 12, any sort of security exploits that could be found in how the Android runtime works could be quickly and easily fixed across the entire Android ecosystem.
To understand how Android's security has improved so much since the early 2010s, it's interesting to take a look at one of the past decade's major Android security scares — 2015's "Stagefright" bug. Stagefright involved an exploit in the Android component used to process media files, which could allow a specially modified video file to run malicious code on Android phones.
One of the scariest Android security bugs of 2015 would be completely neutered by Project Mainline.
While there's no evidence that Stagefright was ever widely used in real-world malware — probably because other security precautions in Android made it very difficult to take advantage of — it was nevertheless big news at the time. In 2015 there was no single silver bullet for Stagefright. Unlike an app-based vulnerability, Google Play Protect couldn't stop bad media files from potentially compromising your phone. The only real fix was to wait for a firmware update and hope for the best.
But if something like Stagefright were discovered in 2021, it would be trivial to address. Google would simply prepare a Project Mainline update for the media playback library and instantly fix the bug across every device running Android 10 and up. With more of Android being modularized in each new version of the OS, it's far less likely that Google will be caught out by an exploit like Stagefright in the future.
Android security patches

As a direct result of the Stagefright bug, in late 2015 Google introduced Android security patch levels, tying a precise date to the level of security in any Google-approved Android firmware. New patches are issued every month, addressing recently discovered security issues, with device manufacturers given a one-to-two-month lead time to get security patches pushed out to devices. The extra visibility of the security patch shone light on the over and under-achieving Android manufacturers, while also giving peace of mind when new updates arrived.
Two years of security updates are now contractually required by Google.
More recently, Google has started to write minimum levels of security support into its contracts with Android manufacturers. The Verge reported in 2018 that phone makers would need to guarantee at least two years of security updates for new phones, with at least four security updates within the first year. By the standards of most high-end phones, that's a pretty basic level of support. But that's just what it is: a bare minimum. Many others at the high end go much further, including Samsung with its recent promise of four years of security updates for major Galaxy phones.
A decade of progress

Between faster Android updates thanks to Project Treble, easier updates to parts of the OS without a full firmware upgrade, longer support lifespans and a strong last defense against malware from Google Play Protect, Android's security today is robust. Most of the highly publicized mobile security risks today come in the form of phishing attacks as opposed to malicious apps or media files. Or in other words, as Android security is strengthened, the bad guys are increasingly opting to trick you, not your phone.
That's not to say the situation around Android security and platform updates is perfect. In an ideal world Google would be just as nimble as Apple when it comes to patching out security vulnerabilities. With Project Mainline we're definitely getting there, but it'll take time for the benefits of the new Mainline modules added in Android 11 and Android 12 to trickle out to the Android ecosystem. Google Play Protect, as good as it is, is limited to neutralizing app-based malware as opposed to other kinds of exploits. And I would definitely argue that the contractual minimum of one security update every three months doesn't go far enough. (Case in point: The dismal update prospects of many cheaper OnePlus Nord phones.)
At the same time, in 2021 the old stereotype of Android being rife with malware and firmware exploits is further from the truth than it's ever been. And direct comparisons with the iOS update model overlook important parts of Google Android like Play Services and Project Mainline. The platform has come a long way since 2011, and the past decade of progress means Android is well-positioned to see off the software threats of the future.

Alex was with Android Central for over a decade, producing written and video content for the site, and served as global Executive Editor from 2016 to 2022.