More research shows exactly what Carrier IQ can, and cannot do
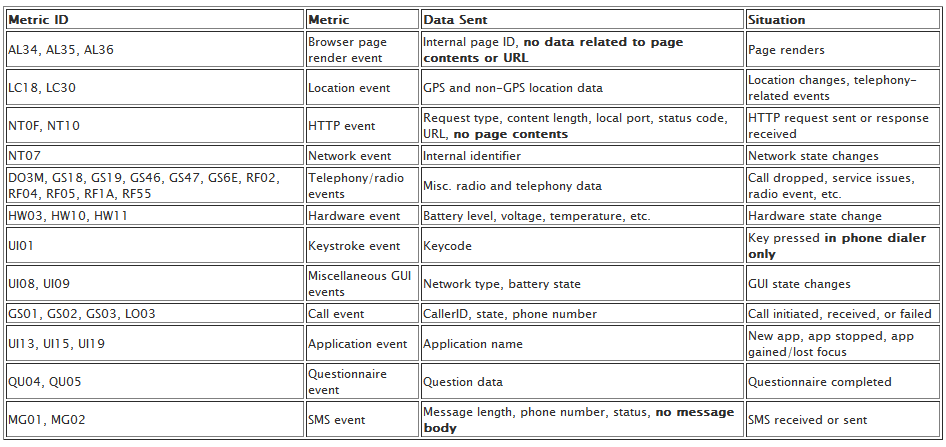
Android hacker and professional security consultant Dan Rosenberg (you may know him as djrbliss from the Internets) has completed his own study on Carrier IQ, and found some interesting results. All those reports about logging keystrokes and spying on SMS messages look to have been blamed on the wrong party, as his research shows that Carrier IQ as written can only capture the data that the carrier sends to it (known as metrics), and even then still has to consult a profile (think of it as a settings page for any app) that a carrier has had CIQ write specifically for their installation. In his own words:
Dear Internet,CarrierIQ does a lot of bad things. It's a potential risk to user privacy, and users should be given the ability to opt out of it.But people need to recognize that there's a big difference between recording events like keystrokes and HTTPS URLs to a debugging buffer (which is pretty bad by itself), and actually collecting, storing, and transmitting this data to carriers (which doesn't happen). After reverse engineering CarrierIQ myself, I have seen no evidence that they are collecting anything more than what they've publicly claimed: anonymized metrics data. There's a big difference between "look, it does something when I press a key" and "it's sending all my keystrokes to the carrier!". Based on what I've seen, there is no code in CarrierIQ that actually records keystrokes for data collection purposes. Of course, the fact that there are hooks in these events suggests that future versions may abuse this type of functionality, and CIQ should be held accountable and be under close scrutiny so that this type of privacy invasion does not occur. But all the recent noise on this is mostly unfounded.There are plenty of reasons to be upset about CIQ, but please don't jump to conclusions based on incomplete evidence.Regards,Dan Rosenberg
So what about all the stuff we see on Trevor Eckhart's video of the EVO in action? It's obviously there, so what's up with all that? We're not security researchers, professional or otherwise, but we are nerds who read about exploits and security every day. The best we can figure is that HTC has exposed those events to the log while sending it as anonymous metric data to the Carrier IQ app. There's still no evidence, and never was, that any of that data is sent anywhere.
The biggest thing to take away from this news is that while Carrier IQ is scary, and many of us consider them evil, they only provide a service to collect data that carriers and OEM's make available. This needs to be made more transparent, because it's never going to go away -- if you don't like it don't use our network, nobody is holding a gun to your head is likely the carriers stance on the subject, and in a way they are right. Our choice in the matter is to not spend our money with them, and heaven knows I understand how unpopular that idea is firsthand. But things are looking more and more like the carriers and manufacturers need to share a good bit of the blame here, and this whole mess is over an easy way to collect data they already have been collecting.
When we get finished here, we can start looking at how the companies who rushed forward shouting "We don't use Carrier IQ on our phones" are collecting the same data with something other than Carrier IQ, so we can be sure that changes are made across the board versus crucifying a small company in Silicon Valley.
Source: Vulnfactory; Pastebin
Get the latest news from Android Central, your trusted companion in the world of Android

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.