Google says 97 zero-day vulnerabilities were exploited in 2023
Most of the zero-day vulnerabilities found last year were in phones, operating systems, and web browsers.

Get the latest news from Android Central, your trusted companion in the world of Android
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- In 2023, there were 97 zero-day vulnerabilities exploited, a significant rise of over 50% compared to 2022 (62 vulnerabilities).
- Analysis by Google's Threat Analysis Group (TAG) and Mandiant revealed that espionage was the primary motive behind 48 out of 58 zero-day vulnerabilities analyzed.
- Criminals focused on end-user platforms like smartphones, operating systems, web browsers, and applications, with a total of 61 zero-days affecting these targets.
Google has found that there were 97 zero-day vulnerabilities that were exploited in 2023, over 50% higher than the number from 2022 (62 vulnerabilities).
Google's Threat Analysis Group (TAG) and Mandiant teamed up to analyze the zero-day flaws revealed last year. Their analysis revealed that out of the 58 zero-days for which they could attribute the threat actor’s motivations, espionage was the main motive for 48 of those vulnerabilities.
Zero-days are essentially flaws that haven't been found by security experts yet. This means IT teams have zero time to fix them before hackers exploit them. That's why hackers love them, because using them doesn't set off any alarms.
Out of all the potential targets, criminals had their sights set on end-user platforms and products like smartphones, operating systems, web browsers, and various applications. Google found that a total of 61 zero-days impacted these targets.
In 2023, Android saw nine vulnerabilities being exploited, up from just three in 2022. On the other hand, iOS faced nine zero-days out in the wild, compared to four in the previous year.
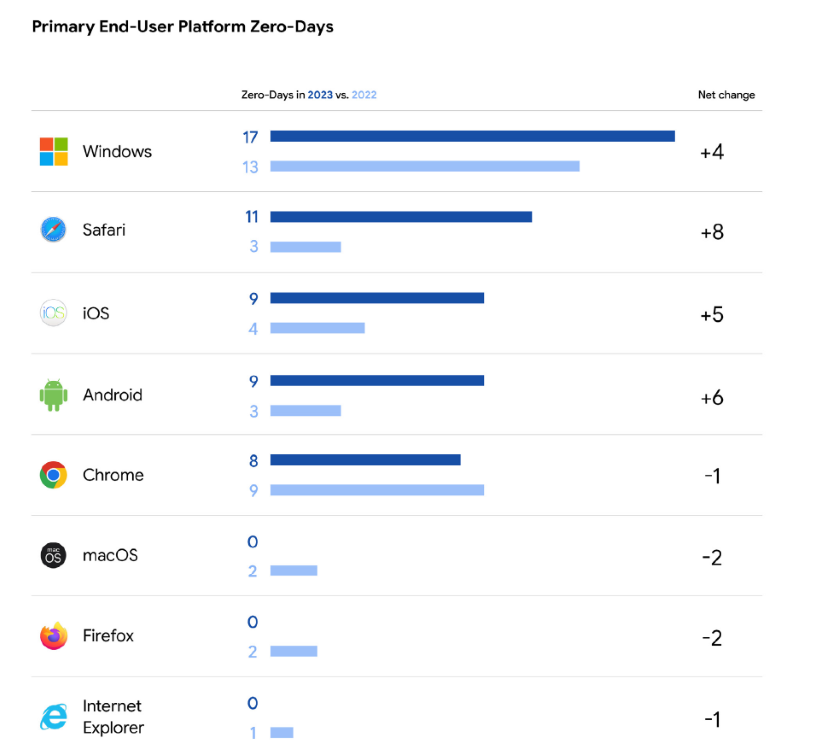
Additionally, there were eight zero-days hitting Chrome and 11 targeting Safari in the wild. Windows takes the lead among the top five, with 17 zero-day vulnerabilities exploited, up from 13 the previous year.
Looking at the findings by region, Google reports that 12 of the zero-days were exploited by Chinese state-sponsored threat actors, with Russia, North Korea, and Belarus following suit. In total, state-sponsored espionage made up 41.4% of the exploited zero-days in 2023.
Get the latest news from Android Central, your trusted companion in the world of Android
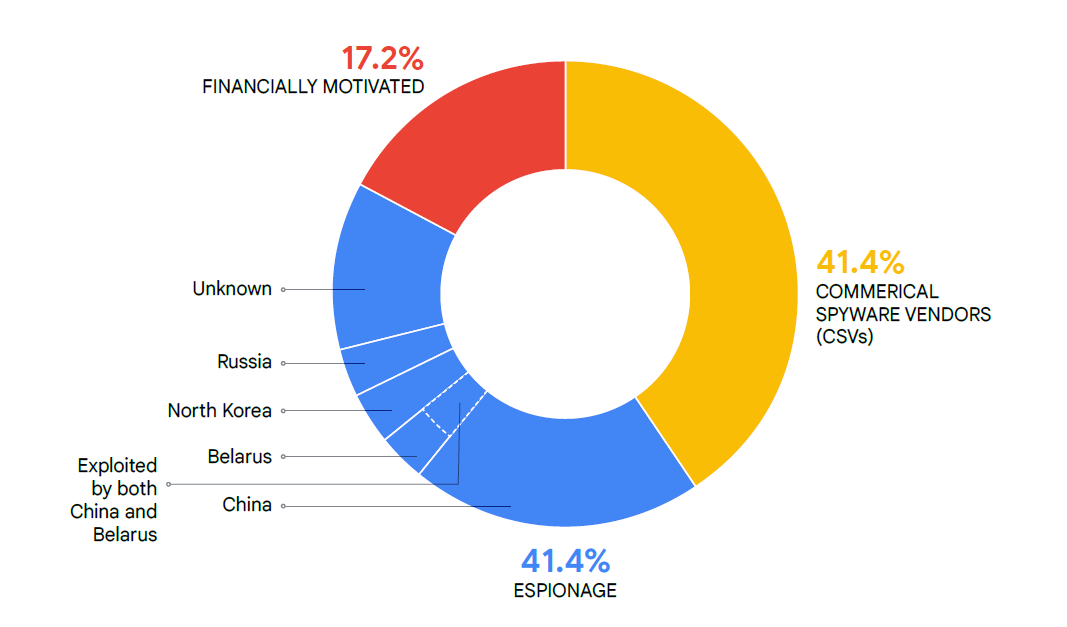
"In 2023, we attributed to commercial surveillance vendors (CSVs) and government espionage actors a combined 48 of 58 zero-days for which we could attribute motivation and only 10 vulnerabilities to financially motivated actors," Google says. "The proportion (roughly 17%) in 2023 of financially motivated exploitation is slightly lower than our observations from 2022, and both of these years were down from the nearly one-third of vulnerabilities we attributed to financially motivated actors in 2021."
That said, investments in exploit mitigations across browsers and operating systems are making it harder for attackers to achieve their goals using certain types of vulnerabilities.
Google's researchers point out that companies like Apple, Google, and Microsoft, who are responsible for end-user platforms, have made significant investments. These investments are clearly affecting the types and quantity of zero-days that attackers can exploit.
Anyway, 2023 saw fewer disclosed zero-day flaws than 2021, which had 106 vulnerabilities. While this might sound like a good thing, researchers think that the rate of zero-day discovery and exploitation will probably stay high compared to the numbers before 2021.

Jay Bonggolto always keeps a nose for news. He has been writing about consumer tech and apps for as long as he can remember, and he has used a variety of Android phones since falling in love with Jelly Bean. Send him a direct message via X or LinkedIn.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
