All about Android's new, safer way of logging into apps
Google added support for wireless U2F cards in a developer version of Google Authenticator back in December. There was an unofficial demo at the Github website that showed how it would work (but it didn't actually work) and the folks at Fidesmo, a company that sells U2F cards, found the APIs buried in the Google Authenticator app. We knew that something would be happening and we just needed to wait for it.
The authentication itself is done in the Google Authenticator app so it's easier on developers who want to use the feature.
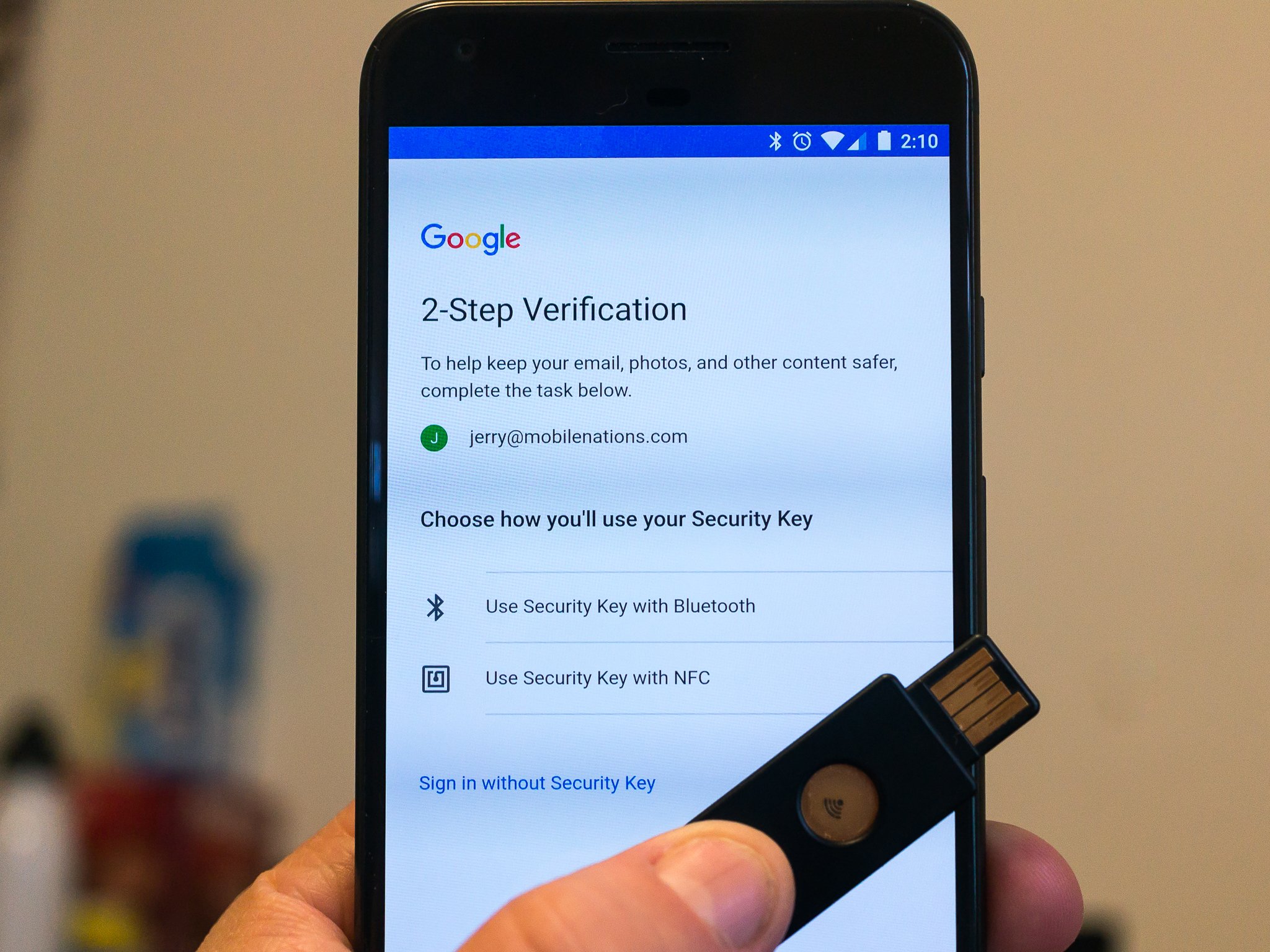
Well, such support has now been expanded, and you can use a wireless security key as a two-factor token when you add your Google account to a phone and U2F works in the Chrome browser independently even without the Google Authenticator app installed. This is a pretty cool thing!
And the way Google is handling it all is pretty cool, too, especially for developers. Rather than have a set of APIs that developers need to use to let users log into their apps and services with a wireless key, the routine is an intent built into the Google Authenticator app. All a developer needs to do is ask for the two-factor token and the Android system takes care of the rest. That means there is no waiting for developers to support anything and it will just work. It doesn't look like the APIs to use the wireless signal for authentication have been opened up for other developers just yet, but we hope that's in the works so apps like Authy will be able to support the feature, too.
What are you talking about?

These. A U2F key is a USB device that can be used as an authentication token. The name stands for Universal Two Factor because it's a standard that anyone making the keys and anyone making a thing that can use them to authenticate is able to incorporate so everything works everywhere. They are a secondary authentication method for people who use two-factor authentication on their accounts.
Read: Two-factor authentication: What you need to know
You should already have two-factor authentication set up on accounts that have the option. It's the easiest way to make sure that someone can't get in and use services in your name without your password and another thing that proves they are you, like a time-sensitive code sent to an app on your phone. A lot of services use two-factor authentication, and setting it up on your accounts will be slightly different for each service. But in the end, it means that when you want to login to something the first time from a new place or a new phone or computer, you need to provide something in addition to your password.
How to set up two-factor authentication on your Google account
Get the latest news from Android Central, your trusted companion in the world of Android
Using a security key can be your main way to authenticate, but even if you would rather use an app or SMS it makes for a great backup in case you lose your phone and need to log in on a computer you've never used to change your password. Adding a security key to a Google account that uses two-factor authentication is easy.
Adding a USB security key to your Google account is easy — and here's how to do it
Once you have added a security key to your account, it works on Android as long as it is NFC or Bluetooth capable. We're not sure if there are any plans to enable U2F over the USB port, but at the time this was written that didn't seem to be supported. There are several different manufacturers of USB security keys that have a wireless option and they all should work the same as long as they use the U2F standard. The one we like and recommend is the YubiKey NEO.
It works as described here with U2F for your accounts, and it can also support OTP (One Time Password) for services that use it, like LastPass. And you can support both U2F and OTP at the same time by using a utility from YubiKey and these instructions.
Using an NFC or Bluetooth security key as your sole 2FA device on Android isn't recommended. It can be done, but there is no reason to not use authenticator tokens through an app, too. But it is a secondary way to have access to all of your 2FA protected accounts and it looks like it's going to be well supported on Android going forward.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.
