How does Android save your fingerprints?

Get the latest news from Android Central, your trusted companion in the world of Android
You are now subscribed
Your newsletter sign-up was successful
The release of an iPhone without a fingerprint sensor has brought along some talk about using fingerprints for authentication and how securely the data is stored. That's awesome. Even if you're not concerned about how it's done, you need a lot of other people to be concerned so that it's done in a way you don't have to worry about!
For starters, Apple uses a similar solution and if you have an older model with a fingerprint sensor you're just as safe using it as you were before. The same goes for older Samsung phones that launched pre-Marshmallow and used Samsung's own methods.
The way Google stores your fingerprint data is the most secure way possible with current tech. It's also fascinating how simple the overview of the whole thing is once you have a look at it. Simple and secure is always a winning combo.

Storage is, by its nature, not very secure. It's the same thing as writing something on a post-it note and putting it in a file cabinet. It's there because it needs to be there, and the best thing you can do is control who has access to it. For a file cabinet, you use a lock, and for your phone, you use encryption. For your fingerprint data, things go one step further: a Trusted Execution Environment (TEE).
A TEE is a separate and isolated area in the phone's hardware. A TEE might use its own processor and memory or it can use a virtualized instance on the main CPU. In both cases, the TEE is fully isolated and insulated using hardware-backed memory and input/output protection. The only way you will be getting in is if the TEE lets you in, and it never will. Even if the phone is rooted or the bootloader unlocked, the TEE is separate and still intact.
A separate processor with its own memory and operating system are used to analyze and store your fingerprint data.
Google uses what they call Trusty TEE to support this. A very small and efficient operating system, appropriately named Trusty OS, runs on the TEE hardware and kernel drivers allow it to communicate with the system. There are Android libraries (you guessed it: the Trusty API) for developers to use so they can ask what amounts to a yes or no question to the TEE. Not just fingerprint data is stored in the TEE. Things like DRM keys and manufacturer's bootloader encryption keys also live in the TEE and work the same way your fingerprint data does — answer whether data presented to it by an application matches the known good data it's storing.
Other manufacturers can use Trusty OS or then can use a different system. As long as all the criteria are met (listed below) and the TEE is isolated and insulated it will meet the security standards needed to use Pixel Imprint (formerly Nexus Imprint).
Get the latest news from Android Central, your trusted companion in the world of Android
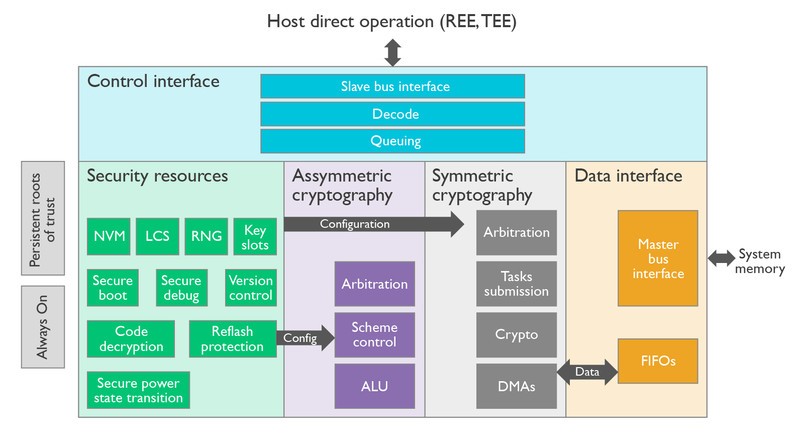
When you register a fingerprint on your Android phone, the sensor grabs the data from the scan. Trusty OS analyzes this data inside the TEE, then creates two things: a set of validation data and an encrypted fingerprint template. This appears to be junk data to everything except the TEE who also has the key to decipher that junk data. This encrypted fingerprint template is stored in an encrypted container either on the TEE or on your phone's encrypted storage. Three encryption layers mean it's nearly impossible to get the data, and even if you could it's useless without a way to decipher it.
Android requires your fingerprint data to be secured with a unique key, and you can;t take it to another phone or reuse it for another user.
The validation data is stored inside the TEE. When you place your finger on the scanner to try and do something, the scanner builds a profile of data. Through the Trusty API, the associated application asks the kernel to ask the TEE if it's right. The TEE checks against the stored validation data using its separate processor and memory, and if enough of the data matches it says yes. If there isn't enough matching data, it says no. This pass or fail response is sent back to the kernel as a software token that the API can read to see the result.
While the TEE itself uses a standalone OS and hardware to stay secure, the fingerprint template uses software-based encryption. It must be signed by a very specific key to be valid. This key is created using device-specific information, user-specific information, and time-specific information. In other words, if you remove a user, change devices or attempt to re-register a fingerprint (the system can tell if you're overwriting an existing fingerprint) the key is no longer recognized and can't be used to decrypt the fingerprint template.
The basic rules that every company making Android phones with a fingerprint sensor have to follow:
- All fingerprint data analyzation must be performed inside the TEE
- All the data associated with a fingerprint must be stored in the TEE or in trusted memory (memory that the main CPU can't even see)
- Fingerprint profile data must be self-encrypted even if stored in encrypted phone storage
- Removing a user account must also securely wipe any data associated with that user's fingerprints
- Where fingerprint profiles are stored must not be visible to any application, process, or user including the root user
- Fingerprint data of any kind must not be backed up to any other source, including the cloud or your computer or any application
- Fingerprint authentication must be used by the process that requested it (no sharing of any fingerprint data, even just the yes or no answer to see if it was correct)
When you have a few standard specifications that are clear, it's not difficult to meet them. This is what makes sure that no matter what Android phone you're using your fingerprint data will be stored safely and no other system process or app can get access to it. As cryptography evolves, especially hardware-backed encryption, so will this method of keeping your fingerprint data safe. It will be interesting to look back once Android Z launches and see how far we've come.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.