Hacking Android Wear: What you can do — and if you should do it at all

Get the latest news from Android Central, your trusted companion in the world of Android
You are now subscribed
Your newsletter sign-up was successful
If it exists, we can hack it — and that includes our Android Wear smartwatches
Android on your wrist is still Android. That means it's still Linux, and people will want to do more than the simple user interface provides. We get it. We paid for these devices, and some of us want to do whatever we want with them. Abuse them. Misuse them. Hack them within an inch of their lives. Then put them all back together like we never touched them. Having your sudo sandwich on every device feels good.
Right now (yes, this very instant!), things are just warming up on the Android Wear hacking front. The devices are new, things are a little different, and everyone who has one is tinkering with it to find out just what can be done. But Android Wear is still Android, and mods and ROMs and hacks will (and are already starting to) happen — especially because the bootloaders are easily unlocked. Thanks, Google.
There are a few things we can already talk about, and they are worth talking about!
Enable developer options and ADB debugging
Your watch needs to communicate with your computer if you want to tickle a few keys and hack at it. To do this you need to enable developer options and ADB debugging on your watch. Google makes that simple, thankfully. You do it just like you did on your phone, though the menu system is a little different.
- Tap the clock on your watch to bring up the Google voice search command
- Keep going to see the menu entries, and get all the way down to Settings
- Tap the Settings entry, then scroll down until you see About and tap it
- Scroll down to the build number, and tap it seven times — yes, just like on a phone
- Go back to the Settings menu and you'll see a new option for Developer Options, and tap it
- In the new list of settings, enable ADB Debugging
To hack your watch you need to enable developer options
Now your watch is ready to talk to your computer over the Android Debug Bridge. That's a part of the Android SDK, and something you might have to set up if you haven't needed it in the past. Google makes that simple, too. Wait — no they don't. That's why we made it simple. Have a read and see how to set up the SDK on your computer.
There's one last thing you will need if you're using a Windows computer — a driver. Installing one is easy, but be aware that some OEM drivers will conflict with the "standard" Google driver. That's why I'll recommend a community-supplied universal driver instead. You can download that from the ClockWorkMod site (thanks, Koush!) right here. If you would rather use Google's driver, you can get that from Google's USB drivers page. Either way, get it installed and reboot your computer just to be safe. Note that OS X and Linux users do not need a separate driver.
Once you have that done, you should check that it works. Place your phone in it's charging cradle, and connect a USB data cable to a primary USB 2.0 or USB 3.0 port on your computer. Open the command prompt or the terminal on your computer, and enter:
Get the latest news from Android Central, your trusted companion in the world of Android
adb devices
Note that you either have to have your PATH set correctly or have the command line open in the folder where adb resides. If you followed our tutorial, your PATH should be set and all will be well.
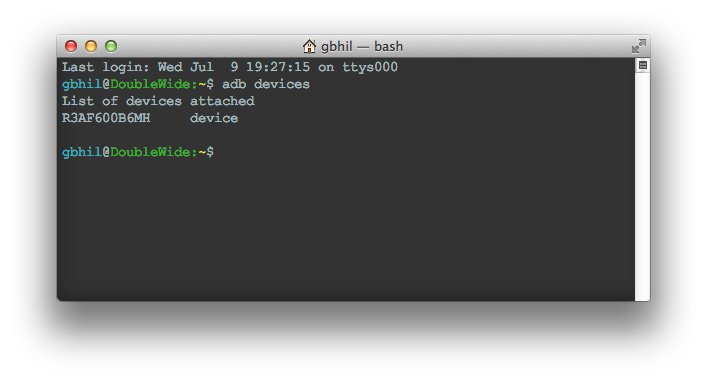
On your phone, you will see a pop up requesting permission for your computer to interact with your watch. Say yes. I always check the box so it never asks me again, but that's up to you. Next type the "adb devices" command again. You should see something like this that shows a device serial number. That means you're good to go!
Unlock your bootloader

This, as always, is the very first thing to do if you are going to want to fiddle around with hacking your Android Wear device. This is because unlocking the bootloader on your watch — just like doing it on your phone or tablet — will erase all of your user data. There's no sense setting things up only to have to set them up again after you unlock your bootloader.
Fastboot oem unlock is your friend.
We'll talk about how to unlock the bootloader in just a second, but — as always — we have to talk security first. This isn't as big an issue as it is with your phone, because your Android Wear watch doesn't have a screen lock. If someone has your phone and your watch, and both are turned on, they will be able to see any and all notifications sent to Android Wear. (Or, we suppose, they could just be standing next to you, looking at your watch.)
As of now, there aren't any apps that store sensitive data on your watch, so having an unlocked bootloader isn't a huge security concern. But it still defeats security and allows anyone to flash anything to your watch. Always keep that in mind.
Got it? Good. Let's unlock stuff so we can break the hell out of it.
You'll need to do one thing on your watch before you unlock the bootloader — pair it with the phone app so you can enable and activate ADB debugging. Technically, this makes unlocking your bootloader the second thing you need to do, but you all know what I mean. You've read how to do that, so go on and do it.
Next, place your watch in its charger and plug in a USB data cable. Connect the other end to a primary USB 2.0 or USB 3.0 port on your computer. Don't use a hub or an extension, because oftentimes that breaks things. Open your command prompt or terminal and type:
adb reboot bootloader
Your watch will reboot to the bootloader, just as seen in the image above. The next step is to issue the unlock command using fastboot, which is installed with the Android SDK. In the same terminal window, type:
fastboot oem unlock
Choose "yes" on your watch by pressing the proper arrow, then choose the circle to confirm, and your bootloader will be unlocked and all personal data will be wiped from the system. When it reboots, re-sync it with your phone through the Android Wear app. Now you can flash stuff. Delicious stuff. Like a custom ROM, perhaps?
(Note that the Samsung Gear Live ignores the "Are you sure you want to unlock this thing?" prompt for some strange reason.)
Sideloading apps

As mentioned, Android Wear is Android. That means that it has basically the same application framework and runtime as your phone does, and you can sideload apps right to your watch using ADB. Ease off the celebration a bit, though, because most apps will install but not work on your watch. That old copy of Flappy Birds you have in Dropbox just isn't going to run. I'm sorry. (No, I'm not).
Don't install apk files from anyone you don't trust
The flip-side of that coin is that because the app framework and runtime are basically the same, crafty people can edit apps so that they do run on the watch, and of course developers can build apps that run on your watch. Because your watch has no access to Google Play or any cloud storage, and has no file browser (yet) you will need to sideload them.
And again (you guessed it) we need to talk about security. Anyone who is able to edit an Android app so it can run on Android Wear can also edit an Android app so it does dirty stuff like send data back to a server, or send texts, or look for naked selfies or any other sensitive data you may have. And when you start sideloading, you might install an app that does store data on your watch. Be safe. Don't install apk files from anyone you don't trust. Ever.
With that out of the way, sideloading apps on your new watch is simple. When you've found an app you want to install, save it to your computer in a folder somewhere, like your desktop. Open your command prompt or terminal inside the folder where you have stored the apk file and enter this command:
adb install
[[ name-of-file ]] .apk
Yes, just like on a phone or a tablet.
Like above, you'll have to had set your PATH correctly to do it this way. If you didn't, there's still an easy fix. Place the .apk file in the same folder that ADB is in (that'd be ../sdk/platform-tools) and make sure your command line is open in that folder. Use the same command.
When it's finished, you'll see that it tells you things were a success, and you can find the application in the main menu under "Start".
Rooting your Android Wear
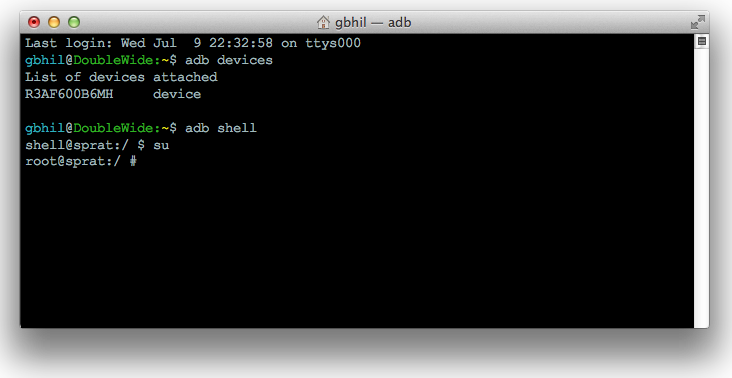
Right now, there's not much you need root for on any Android Wear device. This will change, and by then easy methods and superuser managers will have been updated to work with your watch. You can be sure we'll talk more about it when it happens.
Wait for a reason to root before jumping in
For now, rooting either the G Watch or the Gear Live is done through insecure boot images and scripts. It's clunky, and it involves a lot of trust in someone unless you can pack a boot image yourself. Here's how that works. The needed binaries are copied to the internal storage. You use a script to boot to an insecure boot image in fastboot, then copy these binaries in place. The device then reboots normally.
Afterwards, you'll have root access if you think you need it. For now, I'd advise most folks to just wait until there's a good reason to need root access — and a nice custom recovery image to flash things with.
There is plenty that we just don't yet know about Android Wear and how deep we'll be able to dig into it. Chances are, it will be deep enough to satisfy even the most curious of us all, but we aren't even going to try and predict this future. For now, we can use these few tips and get ready!

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.
