Aviate isn't 'spying' on anyone, it's just being sloppy with your data
Storing your location and installed apps in plain text is at issue here, not collecting that data in the first place
A lot of fuss is being made about the Aviate launcher the past couple days, with things hitting a fever pitch today. Besides the endless requests for invite codes on every social media site known to modern man, it's come to light that the launcher is sharing the data it collects on you with the world. Sort of.
Let's back up a tad. Aviate is a launcher that reconfigures itself — the apps it thinks you need to see right this second — depending on where you are. It's been in private beta for a while, and opened up to more users this week.
The to-do is that your location and list of installed apps are available via a publicly accessible API — but only if you know your unique device identifier. That's not good, but it's not necessarily the end of the world, either.
The good news is that Aviate has said this is something they are fixing, and have made it a top priority. (Update: Looks like the web access has been killed, as promised.) In the meantime, here's what you need to know if you're going to use the app.
Source: +Arvid Gerstmann (1), (2)
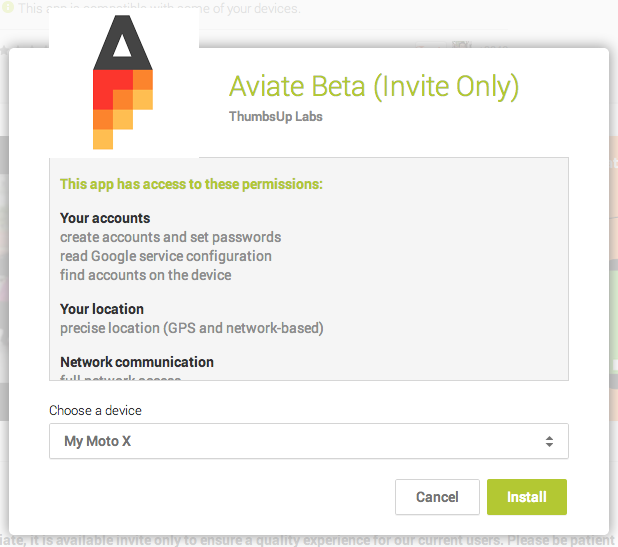
You read the permissions when you installed Aviate, right?
First, let's tackle the data collection. The main points of contention seem to be that the folks at Aviate track which apps you have installed and use — kind of an important thing for a launcher to know — and your precise location via longitude and latitude coordinates. I'm not sure why this surprises (or outrages) everyone, because it needs both these things to do what the app does. And both of these things are declared in the app's list of permissions. In fact, let's have a look at the long list of permissions. As you can see, Aviate asks to do everything except borrow your car.
- Your accounts
- create accounts and set passwords
- read Google service configuration
- find accounts on the device
- Your location
- precise location (GPS and network-based)
- Network communication
- full network access
- view Wi-Fi connections
- view network connections
- receive data from Internet
- connect and disconnect from Wi-Fi
- Your personal information
- read calendar events plus confidential information
- Phone calls
- read phone status and identity
- Storage
- modify or delete the contents of your USB storage
- System tools
- mock location sources for testing
- read Home settings and shortcuts
- write Home settings and shortcuts
- send sticky broadcast
- modify system settings
- test access to protected storage
- Your applications information
- retrieve running apps
- Bluetooth
- pair with Bluetooth devices
- access Bluetooth settings
- Affects Battery
- prevent device from sleeping
- control vibration
- Alarm
- set an alarm
- Sync Settings
- read sync settings
- toggle sync on and off
- Wallpaper
- set wallpaper
- adjust your wallpaper size
Aviate sorts your apps into categories and pages based on time of day, or where you are. When you're at work, you have a work screen with productivity apps. When you're at home, you have entertainment-based apps like Netflix on your screen. Aviate needs to know what apps you have installed — and where you are — to do this. Aviate also makes it very clear in the permissions that the app will be collecting this, and more. If we want an application that shows us apps based on where we are and what we're doing, the app needs to know where we are and what apps we have installed.
Get the latest news from Android Central, your trusted companion in the world of Android
If the location and installed apps list wasn't in plain text, we wouldn't be having this conversation.
This isn't "spying," because you asked Aviate to do it when you installed the app.
The way Aviate stores and transmit this data, on the other hand, is worth questioning.
If you visit a URL at Aviate's site using your device ID, you get a plain-text listing of your location and installed apps. The URL, for those who want to check, is http://www.getaviate.com/search/api/v3/devices/DEVICEID. You can find your device ID in the system's logcat file, or find it by clicking on the "Help" button in the app. Click here for an example if this is all over your head. The issue is two-fold:
- Anyone with a web browser can see your data if they know your unique ID
- Anyone sniffing traffic can see your data because it's in plain text
There is no reasonable excuse for Aviate to do things this way. While your device ID isn't exactly easy to guess, another application developer can get access to it with just a few lines of code. Do you want someone to have the exact location where you — or your kids — sleep every night? I don't.
The Aviate app isn't my cup of tea, and I tried and quickly uninstalled it anyway. But there's a lot of traction behind it, and for a lot of people it does the things they want. The developers have to get this mess straightened out, and soon. They may not be spying on you, but they are sharing the information you gave them with everyone else.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.
