Researchers find that Android phones are prone to new fingerprint attack
The new attack is said to brute force fingerprints to unlock and take control of smartphones.

What you need to know
- Chinese researchers have found that Android phones are vulnerable to new attacks.
- Dubbed BrutePrint, it can unlock any Android phone that uses a fingerprint sensor for authentication.
- It is done by brute forcing fingerprint images obtained by attackers to gain access to devices.
New research findings suggest Android phones are susceptible to fingerprint attacks (via BleepingComputer).
Dubbed BrutePrint, these attacks seem to bypass user authentication and take control of your Android device, per researchers from Tencent Labs and Zhejiang University.
Fingerprint authentication on Android phones generally comes with safeguards, which are associated with users' attempt limits as well as liveness detection, to protect against brute force attacks. The Chinese researchers, however, overcame these safeguards with two zero-day vulnerabilities dubbed Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL).
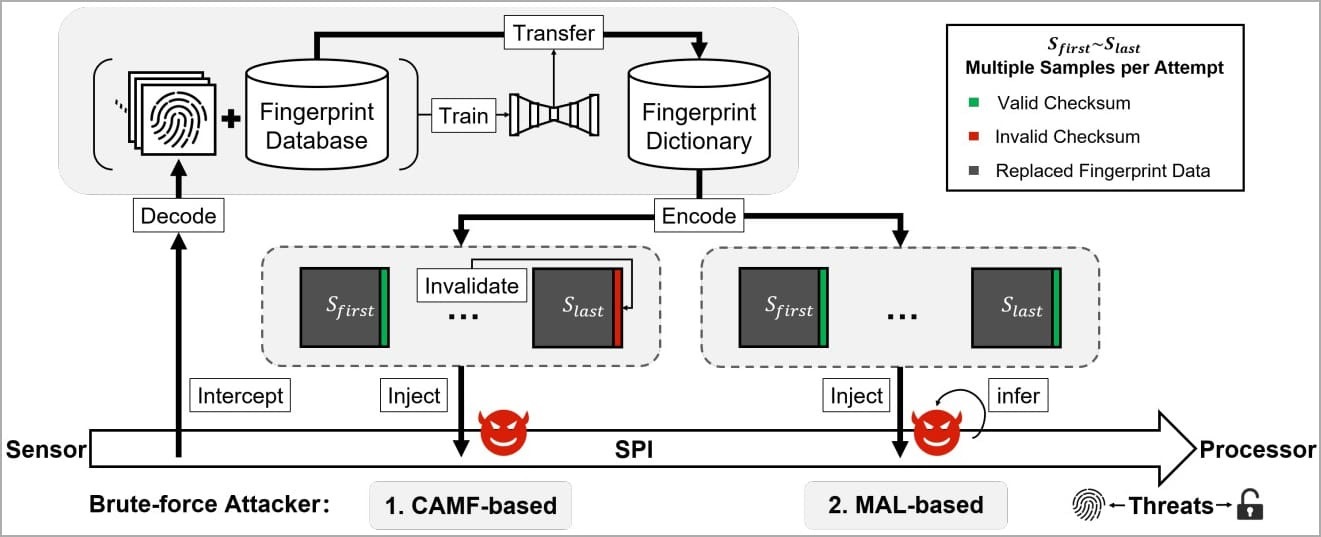
Further, the researchers have found that "biometric data on the fingerprint sensors' Serial Peripheral Interface (SPI) were inadequately protected, allowing for a man-in-the-middle (MITM) attack to hijack fingerprint images," the BleepingComputer report states.
These BrutePrint and SPI MITM attacks, which utilize the user's fingerprint image, were carried out on nearly ten prominent smartphones running on Android, including the Xiaomi Mi 11 Ultra, OnePlus 7 Pro, Huawei devices running on HarmonyOS (Huawei P40), and some iOS devices.
"The tested Android devices allow infinite fingerprint tryouts, so brute-forcing the user's fingerprint and unlocking the device is practically possible given enough time."
Researchers suggest the attacker would need physical access to the phone as well as fingerprint databases, seemingly available from academic datasets or biometric data leaks from the past, notes the report. Moreover, the necessary equipment is said to be available for just $15.
Get the latest news from Android Central, your trusted companion in the world of Android
It was found to take between 2.9 hours to 13.9 hours to complete a BrutePrint attack if the device owner has registered one fingerprint for authentication. This would take significantly less time with more fingerprints registered to the device.
That said, the threat from a BrutePrint attack is not an immediate cause for major concern, as the attacker still needs physical access to the device. That said, it could still be dangerous when it comes to stolen devices, as BrutePrint can then be used to bypass device authentication.
The BleepingComputer further implies that it could raise privacy-related questions regarding investigations conducted by law enforcement, saying they could potentially use the aforementioned techniques to unlock any phone with a fingerprint sensor for authentication.

Vishnu is a freelance news writer for Android Central. Since 2018, he has written about consumer technology, especially smartphones, computers, and every other gizmo connected to the internet. When he is not at the keyboard, you can find him on a long drive or lounging on the couch binge-watching a crime series.
