The definitive ranking of two-factor authentication methods
They're all better than nothing!
Get the latest news from Android Central, your trusted companion in the world of Android
You are now subscribed
Your newsletter sign-up was successful
You should be using two-factor authentication on every account that gives you the option. There is no better way to keep your account secure, and no matter who you are, you should want all of your accounts to be as secure as possible. It also doesn't matter which phone you use — 2FA works with a cheap Android phone, the best Android phone, or an iPhone. Of course, you've heard all of this before.
All two-factor authentication methods are not created equal, though. Like every other user-facing security measure, you have to trade some convenience for protection, and the most secure methods of 2FA are also the least convenient. Conversely, the most convenient methods are also the least secure.
We're going to take a look at the different ways you can use two-factor authentication on devices like the best android phones, and discuss the pros and cons of each.
4. SMS-based two-factor authentication
Getting a text message with a two-factor code is the most popular way to secure an online account. Unfortunately, it's also the worst way.
SMS-based 2FA is easy and convenient. It's also not very secure.
You give your phone number when you sign up for an account, or if you go back and enable 2FA at a later time. Then, after the number is verified, it's used to send a code anytime you need to authenticate that you are really you. It's super easy and convenient, which means plenty of people use it, and many companies offer it as the only means to secure an account.
Ease of use and convenience are great things, but nothing else about SMS is good. SMS was never designed to be a secure means of communication. Nathan Collier, a senior malware intelligence analyst at Malwarebytes, describes SMS like this:
"SMS text messages, sent and stored on servers in plain text, can be intercepted during transit. Moreover, SMS messages can be sent to the wrong number. And when messages reach the correct number, there is no notification from the recipient as to whether the message was read or even received."
Get the latest news from Android Central, your trusted companion in the world of Android
A bigger problem is that carriers can (and have been) tricked into authorizing a new SIM card using the phone number of someone else. So if someone really wanted to get access to your bank account or order a bunch of stuff from Amazon using your credit card; all they need to do is convince someone at your carrier that they're you, you lost your phone, and you need your number moved to a new SIM card that they happen to be holding.
All of this goes for email-based authentication, too. Email is really the only way any account recovery process can work, and plenty of places like your bank will want to send you a code via email to log in from a new device. It's just not very secure, and everyone in the industry knows it. So maybe fixing how email is used as a backbone for this sort of thing is what comes next.
3. Authenticator apps
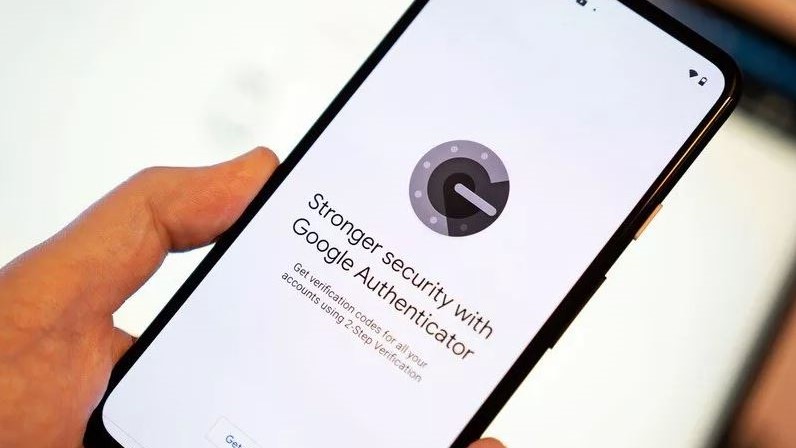
Authentication apps like Google Authenticator or Authy offer a significant improvement over SMS-based 2FA. They work using what's called Time-Based One Time Passwords (TOTP) that an application on your phone can generate using a complex algorithm without any network connection. A website or service uses the same algorithm to make sure the code is correct.
Authenticator apps are better than SMS for 2FA, but they are not foolproof.
Since they work offline, TOTP style 2FA isn't subject to the same problems that using SMS is, but it's not without its own set of flaws. For example, security researchers have shown that it is possible to intercept and manipulate the data you're sending when you enter the TOTP on a website, but it's not easy.
The real problem comes from phishing. It's possible to build a phishing website that looks and acts just like the real thing, and even passes along the credentials you supply, like your password and the TOTP generated by an authenticator app, to log in to the real service. It also logs itself in at the same time and can act as if it were you without the service you're using, knowing the difference. After all, the proper credentials were supplied.
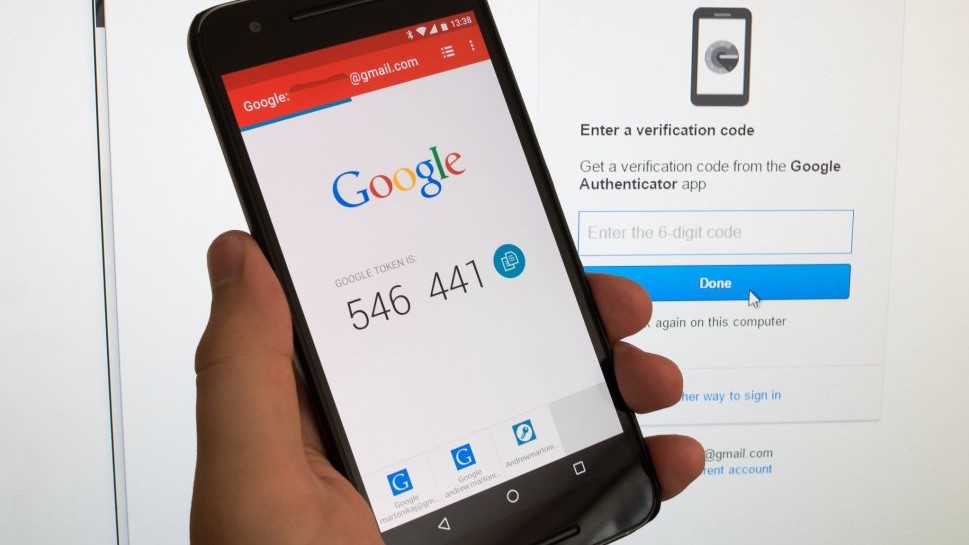
Another disadvantage is that it might not be easy to get the codes you need if you lose your phone. Some authenticator apps like Authy work across devices and use a central password to set things up to be back up and running in no time.
In addition, most companies will provide a set of backup codes you can keep for times when everything goes south. Since that data is also being sent across the internet, it weakens the effectiveness of using TOTP but offers greater convenience to users.
2. Push-based 2FA
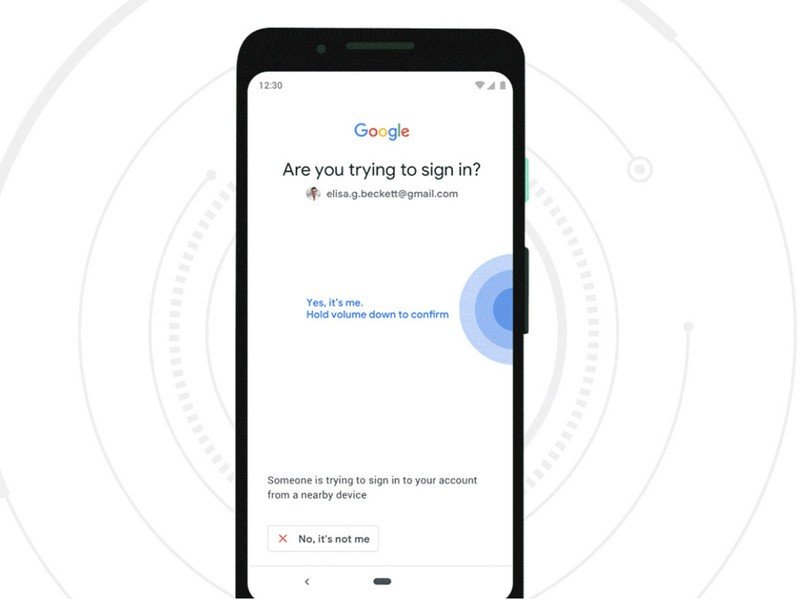
Some services, most notably Apple and Google, can send a prompt to your phone during a login attempt. This prompt tells you that someone is trying to log into your account, can also give an approximate location, and asks you to approve or deny the request. If it's you, you tap a button, and it just works.
A notification for 2FA is super easy and super convenient. Don't lose your phone, though.
Push-based 2FA improves SMS 2FA and TOTP authentication in a couple of ways. It's even more convenient because it all works through a standard notification on your phone — all you need to do is read and tap. It's also much more resistant to phishing and so far has shown to be very "hack" resistant. Never say never, though.
Push-based 2FA also magnifies some of SMS and TOTP's disadvantages: You have to be online through an actual data connection (voice and text cell plans won't work), and you have to be holding the right device to get the message. It's also not very standardized, so you can't always expect to use a login prompt on your Google Pixel to authenticate your other accounts.
Outside of these two genuine drawbacks, push-based 2FA is secure and convenient. It's also going to factor into Google's future plans to enforce 2FA for your Google account.
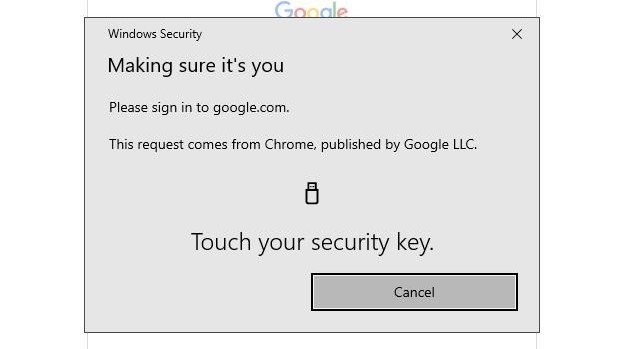
1. Hardware-based 2FA

Using a separate piece of hardware like an authenticator device or a U2F security key is the best way to secure any online account. It's the method I use, so I can tell you that it's not very convenient and makes it not very popular.
You set it up using the hardware, and whenever you want to log in from a new device or after an amount of time set by an account administrator, you need to produce the same device to get back in.
It works by the device sending a signed challenge code back to the server that is specific to the site, your account, and the device itself. So far, U2F has been phish-proof and hack-proof. Again, never say never.
Using a U2F key is the least convenient but most secure way to do two-factor authentication. It's probably not for you because it's a huge PITA.
You can usually set up more than one device on the same account, so you won't lose access if you lose your security key, but it still means that you need to have that key with you every time you want to log in to a website or service.
For example, I use a U2F key to secure my Google accounts, and every 12 hours, I need to provide the key to get back into my Google Enterprise account for work. That means I have a key in my desk drawer, on my keychain, and in an envelope that a friend keeps for me in case of an emergency.
Usually, you can also set up a backup method of 2FA if you're using a key, and Google forces you to do so. This is great for convenience, but it also compromises the security of your account, because the less secure methods are still viable ways for you — or anyone else — to get back in.
Another drawback to using a hardware token like a security key is cost. Using SMS, an authenticator app, or push-based 2FA is free. To use a security key, you'll need to purchase one and they can range from $20 to $100 each. Because you really should have at least one backup key if you're going this route, this can add up.
Finally, using a security key with your phone can be clunky. You'll find keys that work via USB, NFC, and even Bluetooth, but no method is 100% reliable, 100% of the time when using a key with a phone.
Which is best?
All of them and none of them.
Any type of 2FA on an account is better than none at all, and even SMS-based 2FA means you're more protected than you would be if you just relied on a password. If you have the patience, a program like Google's Advanced Protection Program can make your online life very secure and almost worry-free. But you need to weigh the convenience against the security.
Personally, I wish SMS-based 2FA would just go away because even I can hack it. That means you can, too, if you're willing to do a little bit of reading and some copy-pasting. Worse, it means that anyone can hack it, and there are people out there that will take the time and energy to try it on any unsuspecting victim they can find.
In the end, you need to realize that you are a target for online hackers even though you're not a politician or a movie star. This means you really need to take the extra step or two to protect your online accounts. Hopefully, knowing a little more about how the different methods of two-factor authentication work can help you make the right decision.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.