Security
Latest about Security

Best Antivirus Software 2024
By Nicole Johnston published
Looking for some extra protection? Here are the best antivirus programs available in 2022. Each one has been thoroughly tested and comes highly recommended.

Samsung is facing a class action suit over a recent data breach
By Jay Bonggolto published
Samsung is being sued for failing to notify affected consumers about a data breach that occurred in July.

Twitter security flaw may have exposed over 5 million accounts
By Jay Bonggolto published
Twitter has confirmed that a code vulnerability resulted in a security breach that allowed bad actors to obtain data on at least 5.4 million accounts.

T-Mobile to pay $350M to settle a class-action lawsuit following 2021 data breach
By Samuel Contreras published
The carrier will pay $350 million to notify and compensate those affected, plus it must spend $150 million beefing up its security.

Amazon apparently handed Ring footage to the police without consent
By Sewon Hwang last updated
Amazon has leaked video footage from Ring doorbells to law enforcement without alerting the users.

These security flaws could have endangered millions of Android phones
By Jay Bonggolto published
Microsoft discovered some critical flaws in pre-installed Android apps that could have opened a backdoor in millions of devices or allowed attackers to take complete control of them.

Are Wyze products safe?
By Chris Wedel published
Wyze has said that the known security vulnerabilities are taken care of.
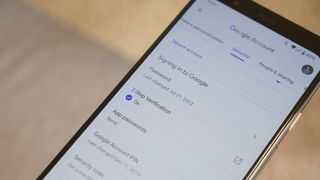
Google is making the web safer with safety status, expanded 2-Step Verification, and more
By Samuel Contreras last updated
Google steps up account protection with better information and automatic 2-Step Verification enrollment.
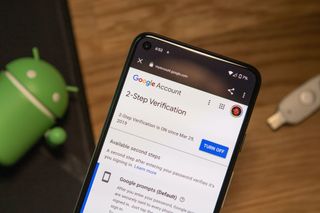
Google wants Chrome and Android to go fully password-free over the next year
By Jay Bonggolto published
Google plans to let Android and Chrome users sign in to any website or app using only a FIDO-certified passkey, as part of a growing effort to eliminate passwords entirely.

How to prepare your Google account for when you pass away
By Jerry Hildenbrand published
Your loved ones have enough to worry about when you shuffle off this mortal coil. Preparing your Google account is easy and something we all need to do.
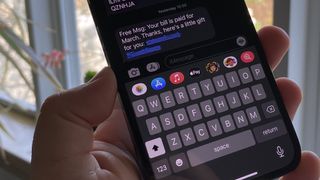
Verizon customers are receiving spam texts from their own number — don't click the link
By Samuel Contreras published
Some customers on Verizon and Verizon-based carriers have received a fake payment confirmation text message from their own number with a bad link included. Do not follow this link.
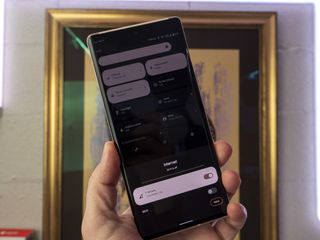
How to be safer on public Wi-Fi
By Samuel Contreras published
Using your phone on public Wi-Fi opens up a lot of questions about security. But if you take a few precautions, you can feel confident about your data security.

Best Smart Home Sensors in 2022
By DJ Reyes, Jeramy Johnson last updated
We've compiled a round-up of the many different sensors you can get to install around your home. From light sensors, to leak sensors to temperature sensors and more.
7 best ways to lock down a kid's phone in 2022
By Nicole Johnston last updated
Use one of these tested apps to control what your child is accessing and how much time they are spending on their cell phone.
Google says account breaches fell by half since turning on 2SV by default
By Jay Bonggolto published
Google reported a 50% decrease in account breaches after automatically enrolling 150 million users in two-step verification last year.

The MY2022 app is a required download for Olympians and looks like a security nightmare
By Jerry Hildenbrand published
To attend or participate in the 2022 Winter Olympics, you need to install the MY2022 app. Unfortunately, it's also riddled with big red flags regarding security and privacy. Here's what we found.

Android 12 quietly gets a useful security feature, but there's a big caveat
By Jay Bonggolto published

T-Mobile reportedly closes out the year with yet another data breach
By Samuel Contreras last updated

T-Mobile says scam calls are up 116%, but so is automatic blocking
By Samuel Contreras published

Upgrade to a tri-band WI-Fi 6 mesh with this Gryphon lightning deal
By Samuel Contreras published
Upgrade your WI-Fi with a tri-band Wi-Fi 6 mesh system from Gryphon. The Gryphon AX has an AX4300 connection with 3,000 square feet of coverage with one node and 5,00 square feet with two.
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android
