Android developers demystify application security (the sky is not falling!)
Get the latest news from Android Central, your trusted companion in the world of Android
You are now subscribed
Your newsletter sign-up was successful
As soon as the schedule for Google I/O 2012's developer sessions was announced, I knew the Security and Privacy in Android Apps session was going to be a must-attend session. The Internet and its FUD machine gives Android security a lot of bad press, and while some of it is warranted, some of it is just sensationalism. Android is a big name and big names in big headlines sell papers.
I'm so glad I felt forced to attend this one. The presenters (Android security engineer Jon Larimer, and Android framework and security engineer Kenny Root) did a wonderful job. It was developer-oriented for sure, but laid out in a way that even novice coders (or rusty old ones) would understand. The gist of it all was typically Google, and typically open -- the tools and methods to provide a very secure Android application are there, developers have to use them correctly. Android's open-market model means there is no one to review every app before it goes in Google Play, and with easy sideloading just about any code can find its way on your device. (Hopefully with your knowledge.) It's up to developers to use the tools to make a safe, secure, and useful application. It might sound like Google is passing the buck on security here, but we have to remember that the alternative is a locked-down garden of corporate evil model like Apple where they control everything that goes in or out of a phone you paid for. I prefer the open model, and I imagine that most of you reading will agree.
The basics, like Android's sandbox, were covered, as well as some outside-the-box thinking, like the risk of Web containers and home-made encryption. We saw examples of how to use the correct app permissions (and only use the correct permissions), developer account security to keep your good name safe and untarnished in Google Play, and even the insecure nature of being online was covered. Larimer and Root did a great job telling the attendees (the room was so crowded they had to turn folks away to meet fire-safety code) about the hazards that exist and the tools to combat them. It was the perfect example of why Google I/O is important to all of us -- developers need to hear this stuff. The short of it:
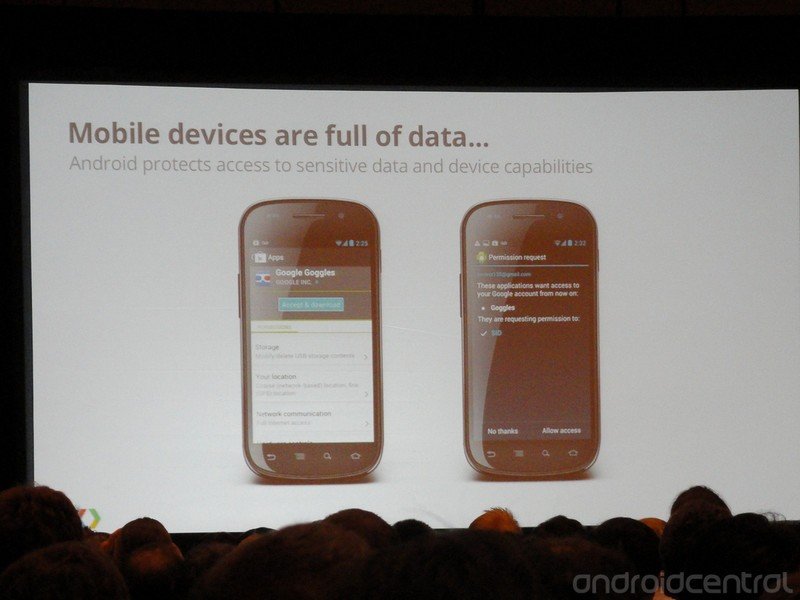
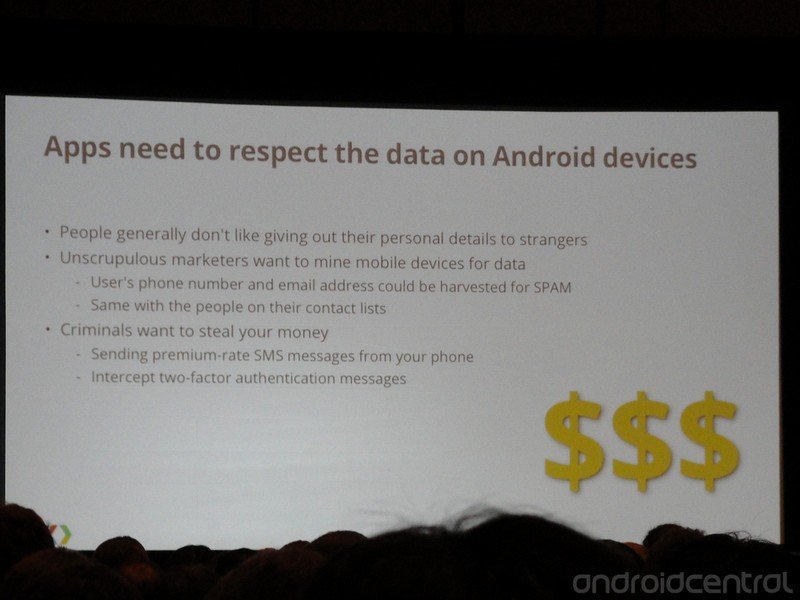
- Our mobile devices are full of very important (to us) and private data.
- Applications must be designed to protect data.
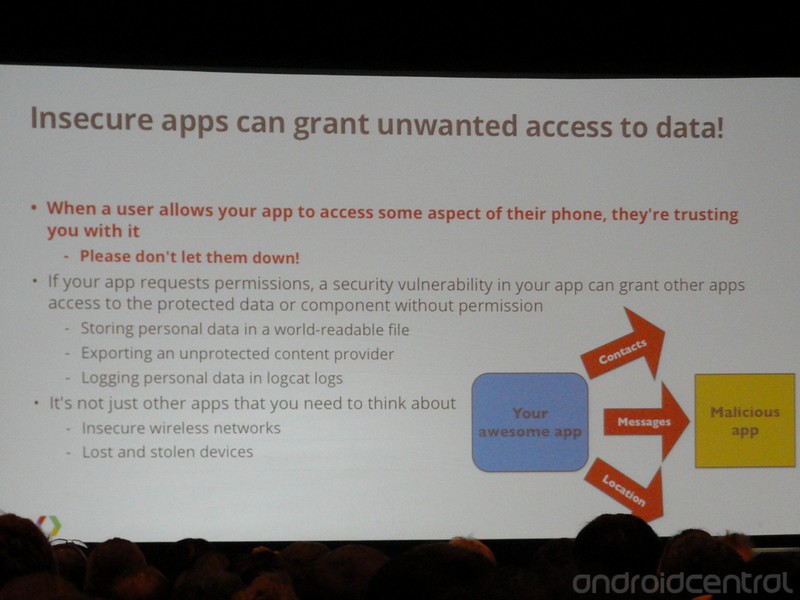
- Any and all data exposed to your application must be kept secure.
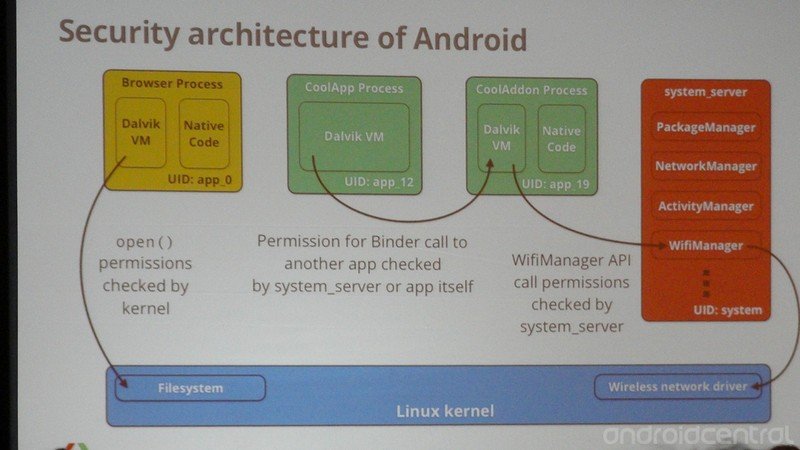
- Android uses application sandboxing and the Linux security and permissions model, so you have to be wary of what other apps are going to ask your app to do for them.
- Permissions are of the utmost importance. Learn what each one does, and only use the ones you must.
- Intents and APIs should be used instead of global permissions.
- Your (the developers) name is on the tin. Spend the time to make sure your product is secure and user info is kept private.
It's a relatively simple set of guidelines, with about a million ways to go wrong. Luckily Google is ready and willing to help with sessions like this as well as various code-jams and developer hangouts across the globe.
What was initially something I thought I had to attend, like it or not, turned out to be the highlight of the entire event for me. Google is serious about application security and your privacy, and they want to help every developer write great apps that keep users data safe and sound. If you're not an Android dev, you can feel good that Google knows what the issues are, and is doing everything they can to keep you safe. If you are a developer, you need to watch this session. We've got the video (about an hour) and a gallery of some highlights after the break.


Have you listened to this week's Android Central Podcast?

Every week, the Android Central Podcast brings you the latest tech news, analysis and hot takes, with familiar co-hosts and special guests.
Get the latest news from Android Central, your trusted companion in the world of Android

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.
