Security
Latest about Security

Lookout to offer premium version with remote lock, wipe
By Jerry Hildenbrand last updated
Scam artists could be hijacking your calls through Google Assistant, Alexa, and Siri
By Jason England last updated
The BBB reports that scam artists are creating fake support numbers and buying their way to the top of search results to trick you and your digital assistant.
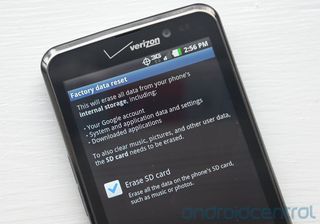
Erase your Android device before getting rid of it [Android 101]
By Phil Nickinson last updated
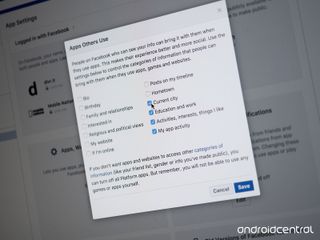
Your apps' default settings don't put your privacy first, so make sure to check them
By Jerry Hildenbrand last updated
Default settings never have your bests interests in mind, so check them out!

Gemalto denies 'massive theft' of SIM card encryption keys by NSA and GCHQ [updated]
By Harish Jonnalagadda last updated

Manage location data in the pictures you take [privacy and security]
By Jerry Hildenbrand last updated
Potential fix for Transformer Prime GPS needs no dongles
By Jerry Hildenbrand last updated

Securing your applications the right way -- the Google how-to
By Jerry Hildenbrand last updated

The malicious 'Godless' exploit found in a few Google Play apps sounds scary, but that's about it
By Phil Nickinson last updated
Another week, another scary-sounding security story. Here's why we wouldn't worry too much about "Godless."

These are the phones that receive regular security patches, according to Google
By Harish Jonnalagadda last updated
Google has committed to working with partners to deliver quick security updates. In its annual review, the company highlighted phones that picked up regular security patches over the course of 2016.

RIM launches BlackBerry Mobile Fusion, Android client now available
By Bla1ze last updated

Q&A: Explaining how the Nexus One was used to take control of a host computer
By Jerry Hildenbrand last updated
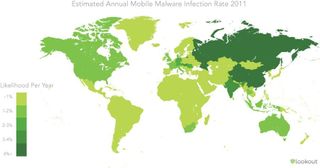
Study shows that 'mobile threat activity' has risen significantly in past 6 months
By Jerry Hildenbrand last updated

Vipre Mobile security app for Android now in public beta testing
By Jerry Hildenbrand last updated
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android




