Security
Latest about Security

How to keep your holiday deliveries safe
By Jeramy Johnson, Courtney Lynch published

Best Free and Paid Parental Control Software in 2022
By Nicole Johnston published
Parental control software helps you set healthy screen time limits, know who your child is talking with and block inappropriate content. Here are my top picks.

3 important steps for keeping your kids safe online in 2022
By Russell Holly published
If you're concerned about keeping your child and their information safe while they enjoy the internet, there are three simple things you can do to protect them.

UK proposes new law to ban the sale of unsecure devices
By Jay Bonggolto published
A new law in the UK will penalize device manufacturers and distributors who manufacture and distribute devices with easy-to-guess default passwords.

Data breaches: What they are, why they're serious, and is your privacy at risk
By Jerry Hildenbrand published
T-Mobile is the latest company to fall victim to a data breach. T-Mobile has specialists paid to take care of its own problems, but what can we do to safeguard our information?

Avast Secure Browser: Assuring your right to online privacy
By AC Staff last updated
For a secure online experience you can trust, Avast Secure Browser is the one you need.

Google will keep Nest devices updated longer than its Android phones
By Michael Allison published
Google today outlined a few of the ways it planned to keep Nest-branded smart home devices secure.
How to use the Google Password Manager on Android and the web
By Ara Wagoner published
Google just made its password manager way more useful on Chrome and Android
By Ara Wagoner published
Google just launched some new important password features on Android and in the Chrome browser.

The 'new' SIM card exploit probably doesn't concern you
By Jerry Hildenbrand last updated
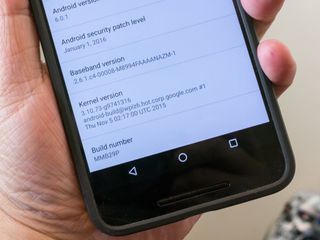
What you need to know about the CONFIG_KEYS Linux kernel vulnerability
By Jerry Hildenbrand last updated
The newest security exploit has arrived, and headlines talk about tens of millions affected. Here's what you need to know.
Geotagging, SD cards and the latest Android privacy/security issue
By Jerry Hildenbrand last updated

App installer exploit affects older versions of Android but isn't as scary as it sounds
By Jerry Hildenbrand last updated
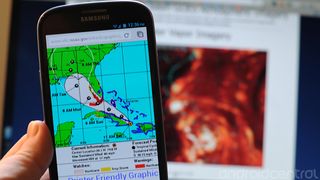
Here comes Hurricane Isaac: Charge 'em if you got 'em
By Phil Nickinson last updated
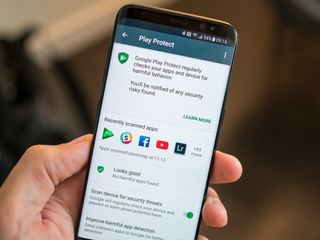
Google releases its 2017 Android security year in review, showing Play Protect has huge impact
By Andrew Martonik last updated
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android